Connecting sources without internet access to OMS
If you implement security policies that restrict computers in your corporate network (corpnet) from connecting to the internet, OMS has an HTTP forward proxy feature called the OMS Gateway that will enable you to still connect computers in your corpnet to OMS.
While the computers in your corpnet will have no connectivity to the internet, the OMS Gateway must have access to the internet, or be connected to a proxy server that does, so as to be able to forward data to the OMS service endpoints. The OMS Gateway supports HTTP tunneling using the HTTP CONNECT command. It collects data on behalf of the OMS agents deployed to the computers in your corpnet, and sends the data to OMS.
The following information will help you understand how to connect sources to OMS that have no connectivity to the internet.
Getting ready
At this time, the OMS Gateway supports the following connected sources scenarios:
- Windows computers directly connected to an OMS workspace with the MMA
- Linux computers directly connected to an OMS workspace with the OMS agent for Linux
- SCOM agent-managed computers reporting to a management group that is integrated with OMS. The following SCOM versions are supported:
- SCOM 2016
- SCOM 2012 R2 with update rollup 3
- SCOM 2012 SP1 with update rollup 7
- Azure Automation Hybrid Runbook Workers
The OMS Gateway feature can also be made highly available using your existing enterprise hardware-based load balancers. To begin, you will need to download and install the OMS Gateway.
How to do it...
You will need to download the OMS Gateway setup file and use the file to install and configure the OMS Gateway. You can also configure high availability for the OMS Gateway using load balancing, if you wish.
Downloading the OMS Gateway setup file
You can download the latest version of the OMS Gateway setup file in one of three ways:
- Navigate to the following URI (https://www.microsoft.com/en-us/download/details.aspx?id=54443) to obtain the setup file from the Microsoft Download Center
- Obtain the setup file from the OMS Portal:
- Sign into your OMS workspace
- Navigate to
Settings|Connected Sources|Windows Servers - In the resulting blade, click
Download OMS Gateway:
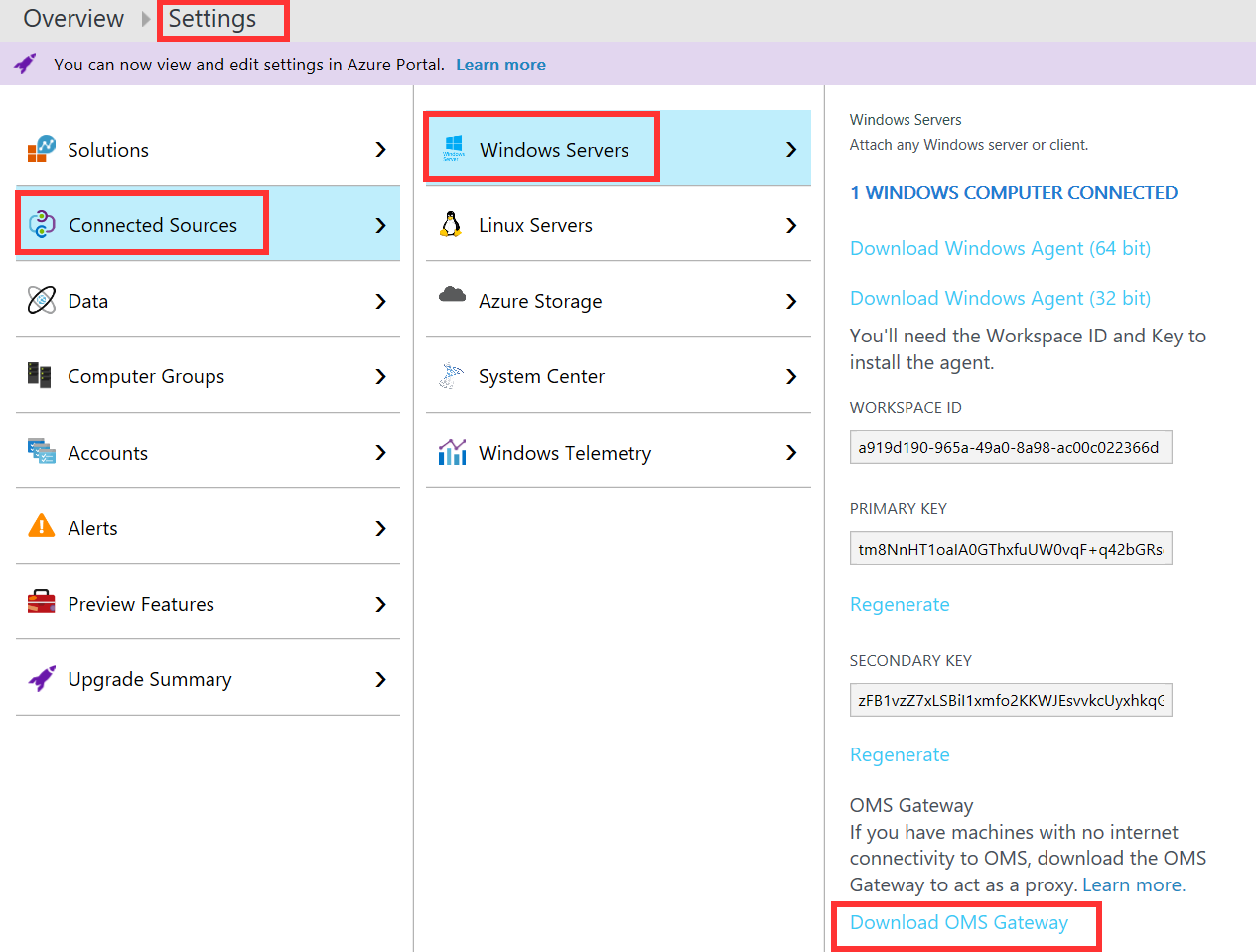
Figure 1.5 Downloading OMS Gateway from the OMS portal
- You can download the OMS Gateway setup file from the Azure portal
- Sign in to the Azure portal
- Select
Log Analyticsfrom the list of services - Select a workspace
- Under the General section in your workspace blade, click
Quick Start. - Under the
Choose a data source to Connect to the Workspace, clickComputers - In the
Direct Agentblade, clickDownload OMS Gateway - Save the
OMS Gateway.msifile:
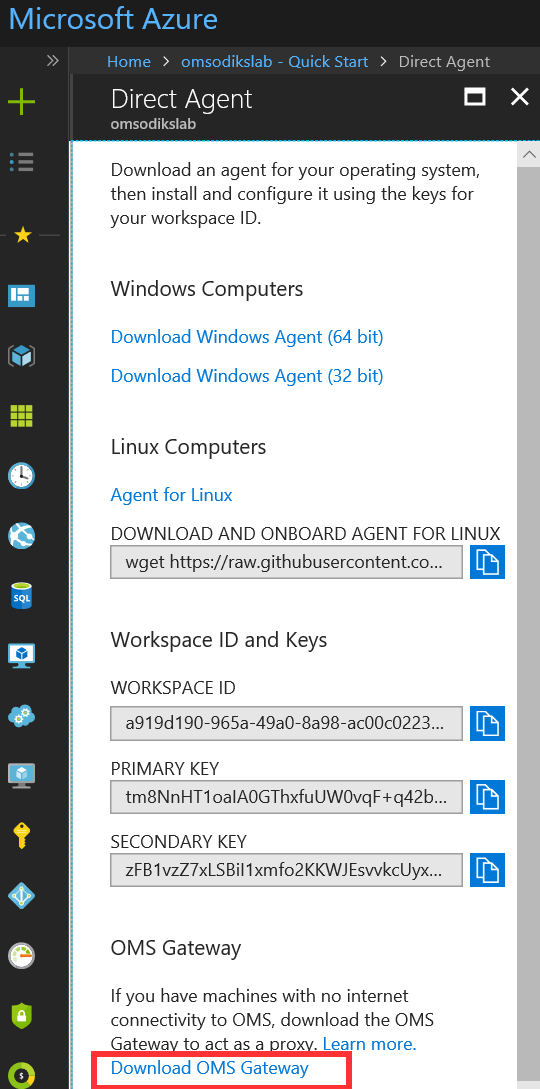
Figure 1.6 Downloading OMS Gateway from the Azure portal
Installing the OMS Gateway
Use the following steps to install the OMS Gateway:
- Locate the
OMS Gateway.msifile downloaded in the previous section - Right-click the file and select
Install - Click
Runon the security warning prompt, if any appear
- Click
Nexton theWelcomepage:
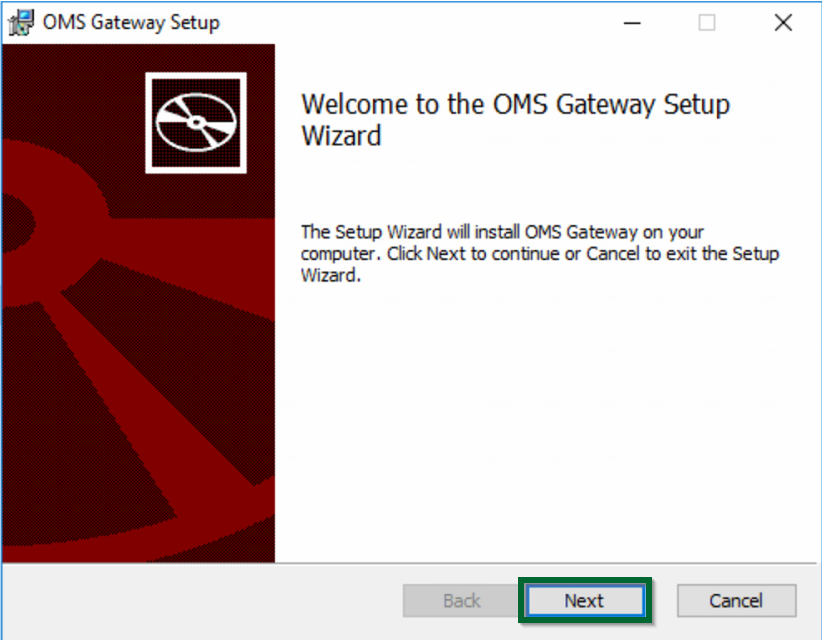
Figure 1.7 OMS Gateway setup
- Select
I accept the terms in the License Agreement in the End-user License Agreementpage and clickNext - On the
OMS Gateway Configurationspage, do the following:- Enter the port to be used for the server. The default port is
8080. You can enter any values that range from1through to65535. - Optionally, if the OMS Gateway server needs to communicate through a proxy to get to the internet, check the radio box to
Use a proxy serverand enter the proxy server information. If the proxy requires authentication, check theMy proxy requires authenticationradio box and enter theusernameandpasswordinformation as well.
- Enter the port to be used for the server. The default port is
- Click
Nextto proceed:
- Click
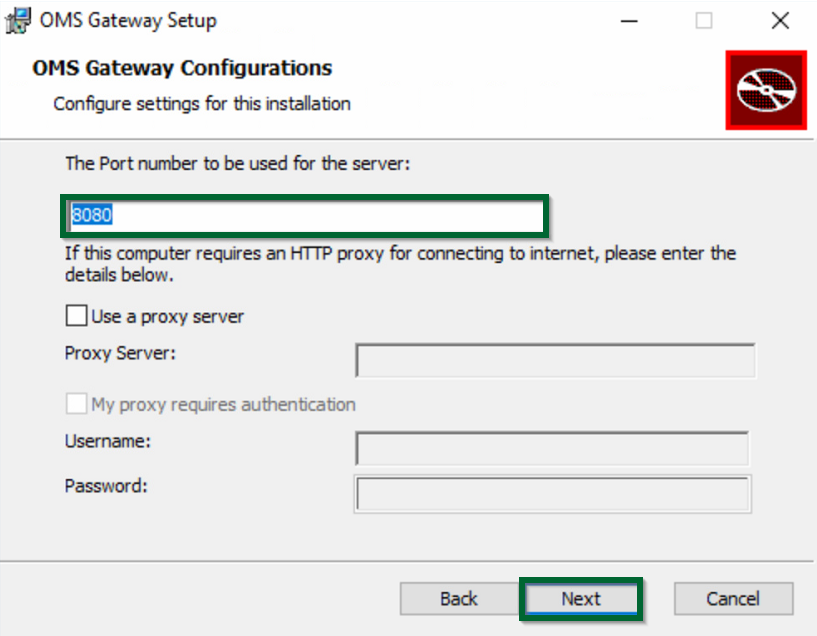
Figure 1.8 OMS Gateway setup
- On the
Destination Folderpage, leave the default folder settings asC:/Program Files/OMS Gateway, or choose another folder to install the OMS Gateway on, and clickNext. - Click
Installon theReady to Install OMS Gatewaypage and selectYesif you receive a User Account Control (UAC) prompt. - Click
Finishafter the setup has completed.
Check the list of services or use PowerShell to verify that the OMS Gateway service is installed and running:
Get-Service OMSGatewayService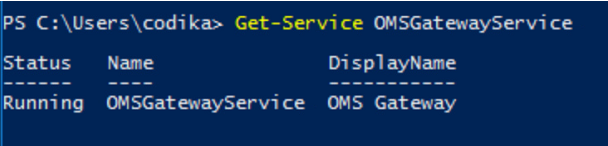
Figure 1.9 Verifying that the OMS Gateway service is running
How it works...
The OMS Gateway is simply an HTTP forward proxy that makes connections on behalf of clients through HTTP CONNECT tunneling. In this case, the OMS agent computer forwards its TCP connection to the OMS Gateway, which tunnels the TCP connection to the OMS service endpoints. This tunneling mechanism means that the data is sent directly from the OMS Gateway to the OMS endpoints without being analyzed.
The OMS Gateway can be used with both OMS agents that are configured to directly connect to an OMS workspace, and an Operations Manager (SCOM) management group that is integrated with OMS. With directly connected OMS agents, the data is sent to the OMS Gateway, which then transfers the data directly to OMS in the manner previously described. When configured for use with an SCOM management group, the proxy information defined for the management group is distributed automatically to every agent-managed computer that is configured as an OMS-managed computer, even if that setting isn't defined.
Depending on the solution(s) configured in OMS, the agent will then collect the relevant data and either send it to the management server or, in the case of high-volume data, such as performance metrics and security events, directly to the OMS endpoints via the OMS Gateway.
There's more...
You can configure the OMS Gateway for high availability through network load balancing (NLB). This will enable you to use the TCP/IP networking protocol to distribute traffic across two or more OMS Gateway servers. Using an NLB configuration will provide you with some measure of high availability and scalability for your OMS Gateway configuration. You can make use of any existing hardware-based load balancers that you use within your infrastructure, and the OMS Gateways configured as NLB hosts should support common NLB configurations, such as your preferred load-balancing algorithms (least sessions, round robin, fastest, and so on), persistence methods, and so on.
Note
Ensure that your target server listening port adheres to the port configuration used during the installation of the OMS Gateway server(s).
You can also install the OMS agent on the computer configured as the OMS Gateway. This configuration will enable the following:
- The OMS Gateway can identify the service endpoints that it needs to communicate with
- The OMS agent can monitor and collect event and performance data from the OMS Gateway
Additionally, Operations Manager Gateway servers deployed in untrusted networks cannot communicate with the OMS Gateway. They can only report to an Operations Manager management server, and would therefore be subject to the proxy server settings (if any) configured for the management group to which the SCOM management server belongs.
For directly connected computers to send data to the OMS Gateway, they must have network connectivity to the OMS Gateway, and the agents' proxy configuration should be set to the same port used by the OMS Gateway to communicate with OMS service endpoints.
Using a proxy server to access OMS from SCOM
Perform the following steps:
- Open the SCOM console and navigate to the
Administrationworkspace
- Navigate to
Operations Management Suite, clickConnection,and then clickConfigure Proxy Server:
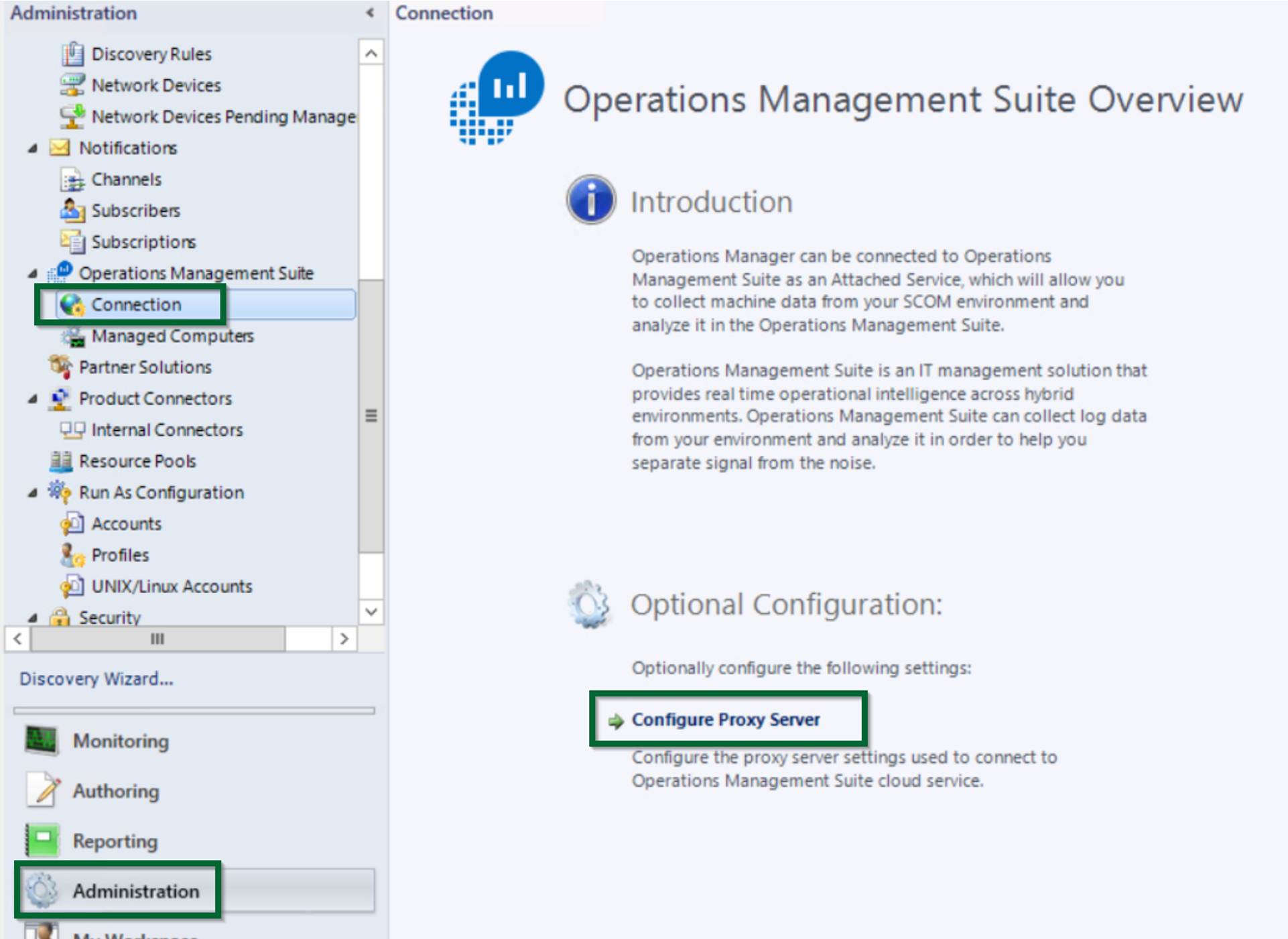
Figure 1.10 - Configuring proxy server options in SCOM
- Select the option to
Use a proxy server to access the Operations Management Suiteand type either the IP address of the standalone OMS Gateway server or the virtual IP address of the array of load-balanced OMS Gateway servers
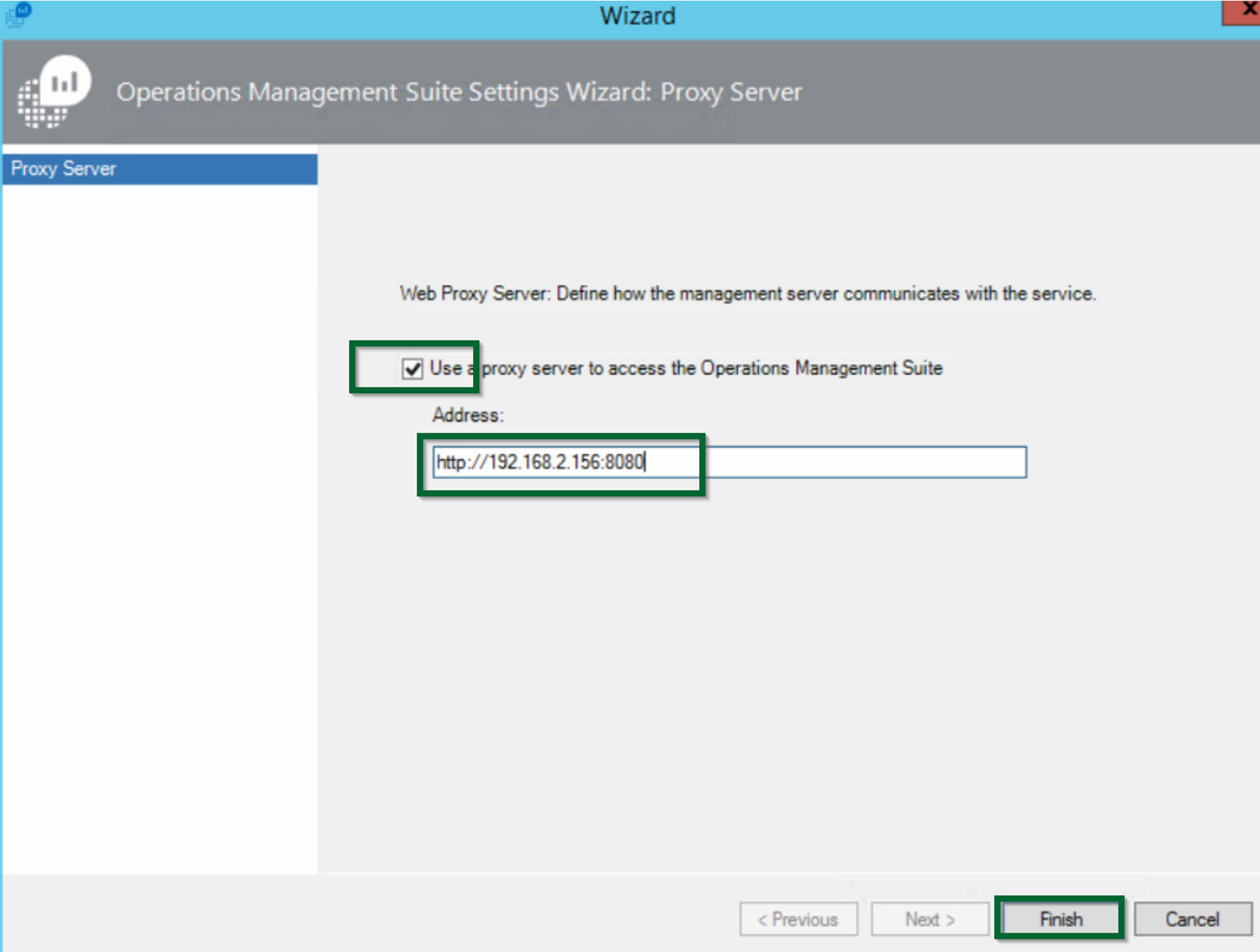
Figure 1.11- Configuring the proxy server in SCOM
Note
Ensure that you start with the http:// prefix. Additionally, ensure that you bypass the HTTPS inspection if you need to permit access to OMS service endpoints through your firewalls.
Use PowerShell cmdlets with OMS Gateway
You can make use of PowerShell to review and modify the OMS Gateway configuration settings. The OMS Gateway PowerShell module should get imported in the OMS Gateway server(s) upon installation of the OMS Gateway feature. You can always verify this by importing the module to confirm:
Import-Module OMSGatewayOnce you confirm that the OMS Gateway has been imported, you can also verify your OMS Gateway configuration for the listening port, log level, and other settings:
Get-OMSGatewayConfig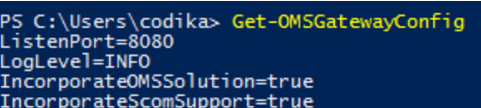
Figure 1.12 - Reviewing the OMS Gateway configuration
To make changes to the OMS Gateway configuration using PowerShell, you can make use of the Set-OMSGatewayConfig cmdlet. For instance, to change the port on which the OMS Gateway is listening, you can execute the following command:
Set-OMSGatewayConfig -Name ListenPort -Value [port]In the preceding command, [port] is the integer value of your desired port on which the OMS Gateway listens.
At this time, the Set-OMSGatewayConfig cmdlet supports the following configuration names:
ListenPortLogLevelIncirporatedOMSSolutionUseIpv6IncorporatedScomSupport
See also
The following links also provide some useful guidance on troubleshooting tips relating to the OMS Gateway:
- Microsoft TechNet: Troubleshooting OMS Gateway event IDs: https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-oms-gateway
- Microsoft TechNet: OMS connectivity resources: https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-windows-agents







































































