Using WebScarab
WebScarab is another web proxy full of features that may be interesting to penetration testers. In this recipe, we will use it to spider a website.
Getting ready
In its default configuration, WebScarab uses port 8008 to capture HTTP requests, so we need to configure our browser to use that port in the localhost as a proxy. We follow steps similar to those of the OWASP ZAP and Burp Suite configurations in the browser; in this case the port must be 8008.
How to do it...
WebScarab can be found in Kali's Applications menu; go to 03 - Web Application Analysis | webscarab. Alternatively, from the terminal, run the webscarab command. Proceed with the following steps:
- Browse to the BodgeIt application of
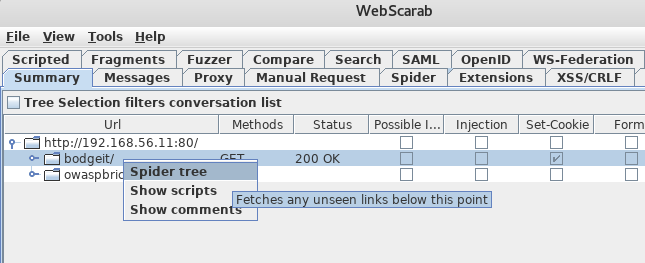
vulnerable_vm(http://192.168.56.11/bodgeit/). We will see that it appears in theSummarytab of WebScarab. - Now we right-click on the
bodgeitfolder and selectSpider treefrom the menu:
- All requests will appear in the bottom half of the
Summaryand the tree will be filled as the spider...





































































