Using the ZAP proxy to view and alter requests
OWASP ZAP, similar to Burp Suite, is also more than a web proxy. It not only intercepts traffic; it also has lots of features like the crawler we used in previous chapters, a vulnerability scanner, a fuzzer, and a Brute Force. It also has a scripting engine that can be used to automate activities or to create new functionality.
In this recipe, we will begin the use of OWASP ZAP as a web proxy, intercept a request, and send it to the server after changing some values.
How to do it...
Start ZAP and configure the browser to use it as a proxy. Further, carry out the following steps:
- Go to OWASP Bricks in the
vm_1and select content exercise number four (http://192.168.56.11/owaspbricks/content-4/):
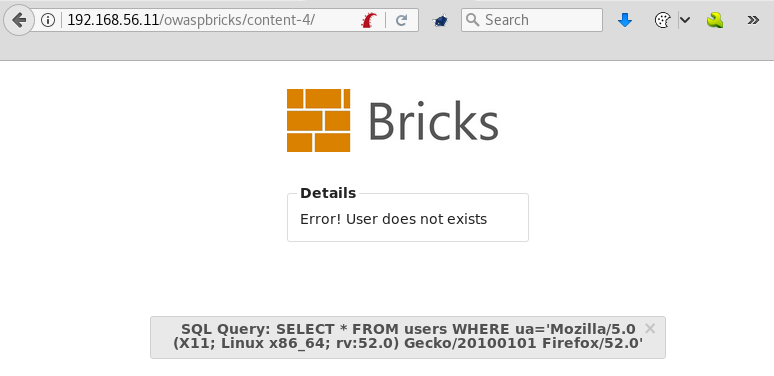
We can see that the immediate response of the page is an error saying that the user does not exist. There is also SQL code displayed, showing that the application is comparing a field (ua) with a string that is the User-Agent header sent by the browser.





































































