Exploiting HTTP parameter pollution
An HTTP parameter pollution (HPP) attacks occurs when an HTTP parameter is repeated multiple times in the same request and the server processes in a different way each instance, causing an unexpected behavior in the application.
In this recipe, we will demonstrate how HPP can be exploited and will explain how it can be used to bypass certain security controls.
How to do it...
For this recipe, we will use bWApp again as it has a very illustrative example of HPP:
- Log in to bWApp in our vulnerable VM and go to HPP (
http://192.168.56.11/bWAPP/hpp-1.php). - Use the normal flow first; there is a form that asks for a name. When a name is submitted, it requires the user to vote for a movie, and, in the end, the user's vote is displayed.
- Note that all parameters (
movie,name, andaction) are in the URL in the last step. Let's add a second movie parameter with a different value at the end of the URL, as shown in the following screenshot:
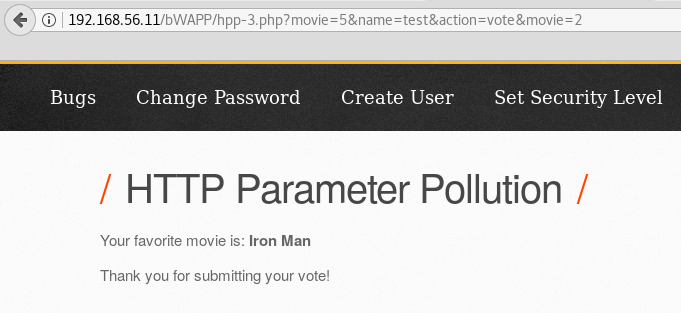
It seems like the server takes only...





































































