Exploiting DOM XSS
Also referred to as client-side XSS, DOM XSS is named this way because the payload is received and processed by the DOM of the browser, which means that the injected code never reaches the server and any server-side validation or encoding is ineffective against this kind of attack.
In this recipe, we will analyze how this vulnerability can be detected and exploited in a web application.
How to do it...
The following are the steps for detecting and exploiting this vulnerability in a web application:
- In the vulnerable virtual machine
vm_1, go toMutillidae II|Top 10 2013|XSS|DOM|HTML5 local storage. - This exercise shows a form that stores information in the browser's local and session storage. Enable the
Developer Toolsin theNetworktab.
- Try adding some data and notice how there is no network communication, and that the green bar displays the value given to the key:
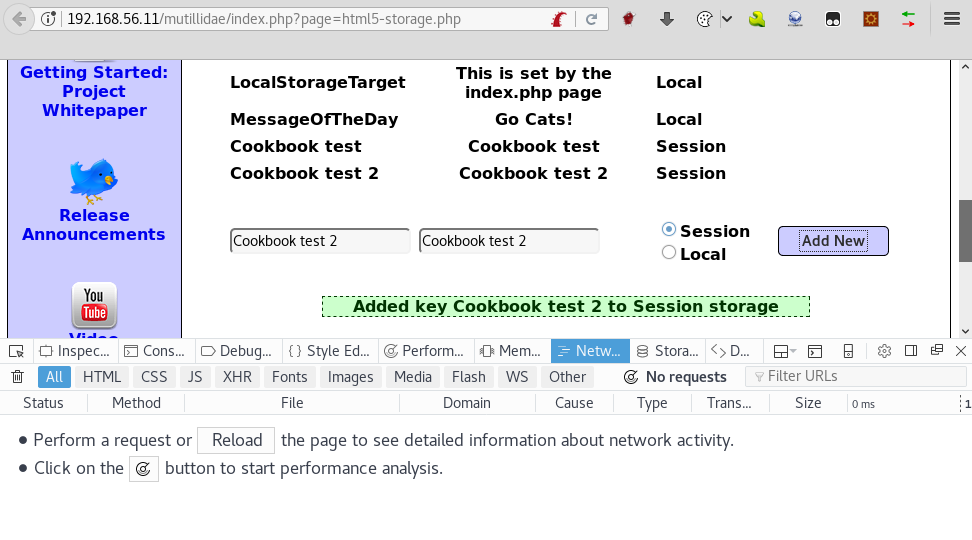
- If we inspect the
Add Newbutton, we see it calls a function,addItemToStorage, when clicked:
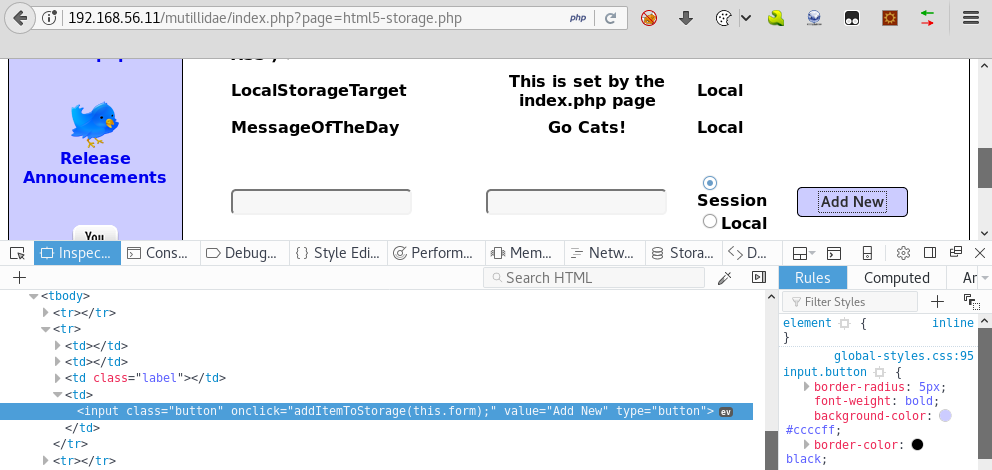
- Now, go to...





































































