Scanning and identifying services with Nmap
Nmap is probably the most used port scanner in the world. It can be used to identify live hosts, scan TCP and UDP open ports, detect firewalls, get versions of services running in remote hosts, and even, with the use of scripts, find and exploit vulnerabilities.
In this recipe, we will use Nmap to identify all the services running on our target application's server and their versions. For learning purposes, we will do this in several calls to Nmap, but it can be done using a single command.
Getting ready
All we need is to have our vulnerable vm_1 running.
How to do it...
All of the tasks in this recipe can be done via a single line command; they are shown separately here to better illustrate their functionalities and results:
- First, we want to see whether the server is answering to a ping or if the host is up:
# nmap -sn 192.168.56.11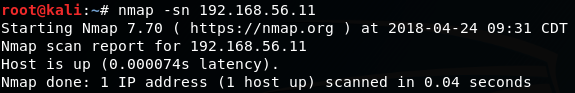
- Now, that we know that it's up, let's see which ports are open:
# nmap 192.168.56.11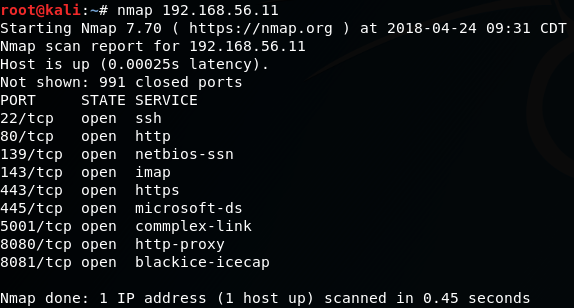
- Now we will tell Nmap to ask the server...





































































