Creating a client virtual machine
Now, we are ready to create our next virtual machine; it will be the server that will host the web applications we'll use to practice and improve our penetration testing skills.
We will use a virtual machine called OWASPBroken Web Apps (BWA), which is a collection of vulnerable web applications specially set up to perform security testing.
How to do it...
OWASP BWA is hosted in SourceForge, a popular repository for open source projects. The following steps will help us in creating a vulnerable virtual machine:
- Go to http://sourceforge.net/projects/owaspbwa/files/ and download the latest release of the
.ovafile. At the time of writing, it isOWASP_Broken_Web_Apps_VM_1.2.ova:
- Wait for the download to finish and then open the file.
- VirtualBox's import dialog will launch. If you want to change the machine's name or description, you can do so by double-clicking on the values. Here, you can change the name and options for the virtual machine; we will leave them as they are. Click on
Import:
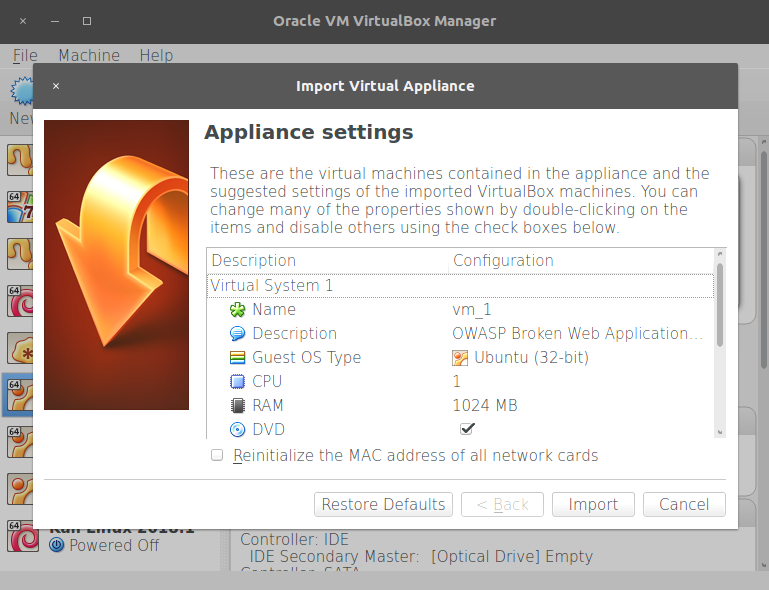
- The import should take a minute and, after that, we will see our virtual machine displayed in VirtualBox's list. Let's select it and click on
Start. - After the machine starts, we will be asked for a login and password; type
rootas the login, andowaspbwaas the password, and we are set.
How it works...
OWASP BWA is a project aimed at providing security professionals and enthusiasts with a safe environment to develop attacking skills and identify and exploit vulnerabilities in web applications, in order to be able to help developers and administrators fix and prevent them.
This virtual machine includes different types of web applications; some of them are based on PHP, some in Java. We even have a couple of .NET-based vulnerable applications. There are also some vulnerable versions of known applications, such as WordPress or Joomla.
See also
There are many options when we talk about vulnerable applications and virtual machines. A remarkable website that holds a great collection of such applications is VulnHub (https://www.vulnhub.com/). It also has walkthroughs that will help you to solve some challenges and develop your skills.
In this book, we will use another virtual machine for some recipes, bWapp bee-box, which can be downloaded from the project's site: https://sourceforge.net/projects/bwapp/files/bee-box/.
There are also virtual machines that are thought of as self-contained web penetration testing environments, in other words, they contain vulnerable web applications, but also the tools for testing and exploiting the vulnerabilities. A couple of other relevant examples are:
- Samurai web testing framework: https://sourceforge.net/projects/samurai
- Web Security Dojo: https://www.mavensecurity.com/resources/web-security-dojo






































































