Exploiting an XML External Entity injection
XML is a format mainly used to describe the structure of documents or data; HTML, for example, is a use of XML.
XML entities are like data structures defined inside an XML structure, and some of them have the ability to read files from the system or even execute commands.
In this recipe, we will exploit an XML External Entity(XEE) injection vulnerability to read files from the server and remotely execute code in it.
Getting ready
We suggest that you read the Abusing file inclusions and uploads recipe before doing this.
How to do it...
Refer to the following steps:
- Browse to
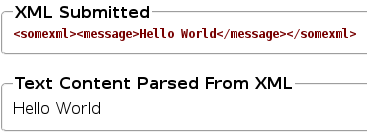
http://192.168.56.11/mutillidae/index.php?page=xml-validator.php. - It say it is an XML validator. Let's try to submit the example test and see what happens. In the
XMLbox, put<somexml><message>Hello World</message></somexml>and clickValidate XML. It should only display the messageHello Worldin the parsed section:
- Now, let's see whether it processes entities...





































































