Bypassing client-side controls using the browser
Processing in web applications happens both on the server side and the client side. The latter is often used to do things related to how information is presented to the user; also, input validation and some authorization tasks are performed client-side. When these validation and authorization checks are not reinforced by a similar server-side process, we may face a security problem, as client-side information and processing is easily manipulable by users.
In this recipe, we will see a couple of situations where a malicious user can take advantage of client-side controls that are not backed up by server-side counterparts.
How to do it...
Let's look at a practical example using WebGoat:
- Log in to WebGoat and go to
Access Control Flaws|LAB Role Based Access Control|Stage 1: Bypass Business Layer Access Control:
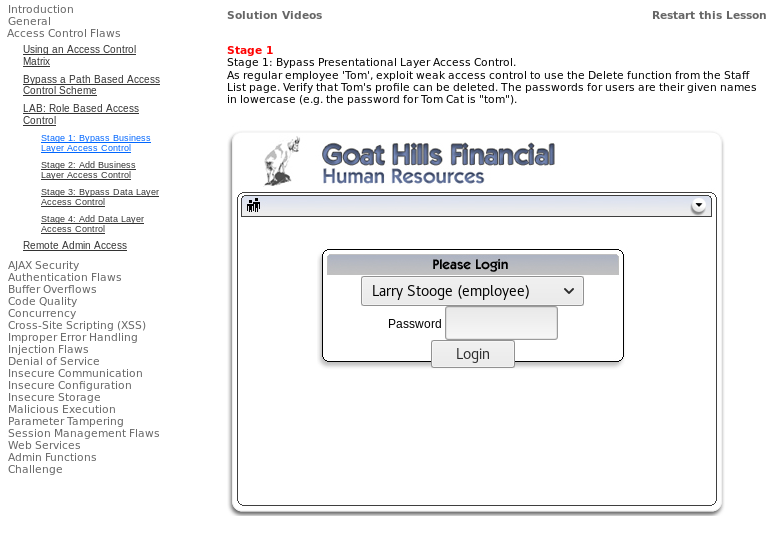
- Use Tomcat's credentials (
Tom:tom) to log in and enable Firefox'sDeveloper Tools(F12). - Let's inspect the list of employees. We can see...





































































