Locating smart TCP attacks
Another type of attack is when you send unknown TCP packets, hoping that the device under attack will not know what to do with them and hopefully pass them through. These types of attacks are well known, and blocked by most of the modern firewalls that are implemented in networks today; but still, I will inform you about them in brief.
Getting ready
What I usually do when I get to a new network is to connect my laptop to the network and see what is running over it. First, I just connect it to several switches and see the broadcasts. Then I configure a port-mirror to critical servers and communication lines and look what is running over it.
To look for unusual traffic, port-mirror the communication links and central servers, and check for unusual traffic patterns.
How to do it
The traffic patterns you should look for are:
- ACK scanning: Multiple ACKs are sent usually to multiple ports in order to break the existing TCP connections
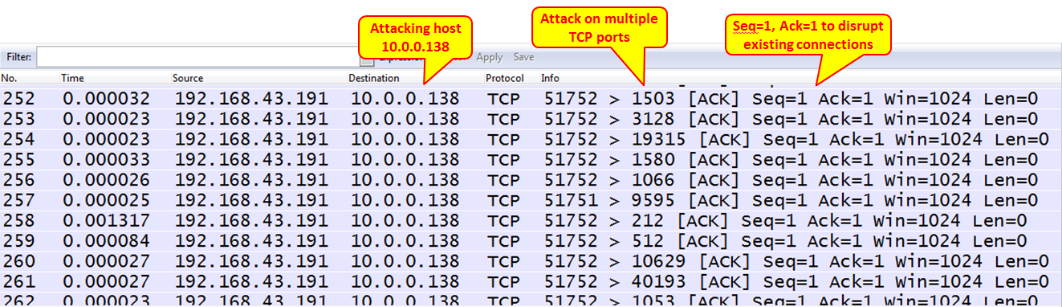
Figure 19.15: TCP ACK scanning
- Unusual flag...




































































