Issues with authentication
Consider the following example in which Person A needs to send a message to Person B, but there might be some issues in checking the authenticity of the sender:
- Authenticity: Person B should identify that the message is from Person A
- Secrecy: Others (Person C) should not sniff the message
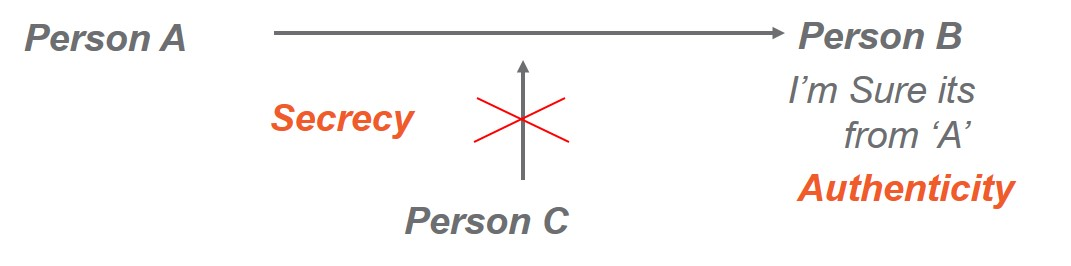
The solution to this problem is using the encryption algorithms.
Encryption
To ensure that data transfer is secure, the computer security systems adopt a mechanism known as encryption. Encryption is the process of converting a plaintext message into ciphertext, where only the person with the decryption key can read the ciphertext. Encryption enforces confidentiality on a computing system, and uses mathematical algorithms to scramble data. The scrambled data, after encryption, is known as ciphertext.
To read an encrypted file, use the decryption or secret key to open the message back into plaintext. This process is known as decryption. The efficiency of encryption depends on your choice...




































































