Implementing Cisco AAA - authentication
AAA can be implemented in two forms: either locally on a device or with TACACS+ or RADIUS.
Implementing authentication using local services
In this section, we going to take look at implementing authentication on the Cisco IOS router. This feature will enable the router to act as an authentication server with all of the user accounts that are created and stored on the device itself:
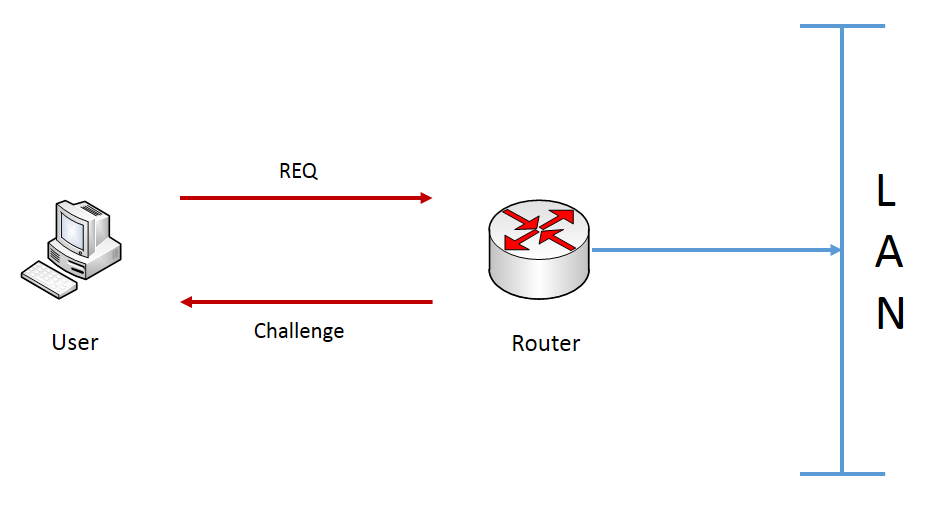
Whenever a user tries to log in, the router will query the local database to validate if the username and password combination exists and is accurate. If yes, this proves to the router that the user has validated their identity and is who they say they are.
The following are the steps to enable AAA using local services:
- Enable AAA on the routers. On the CLI, use the following command. This command enables AAA and unlocks all other subcommands:
Router enable Router # configure terminal Router(config) # aaa new-model
- Enable the username and password. The next step after you enable...




































































