Why DHCP snooping?
DHCP snooping is a feature that exists on a switch. It creates two types of ports: trusted and untrusted. When DHCP snooping is enabled on a switch, all ports are labeled as untrusted, and this prevents any DHCP Offer and DHCP ACK messages from entering the switch. However, the port that is connected to the DHCP server should be configured manually as a trusted port. The trusted port allows the DHCP Offer and DHCP ACK messages to enter the switch.
The DHCP snooping feature is a countermeasure against any rogue DHCP server that may be attached to the network infrastructure.
Note
DHCP snooping is enabled on the VLAN level on a switch.
Trusted and untrusted sources
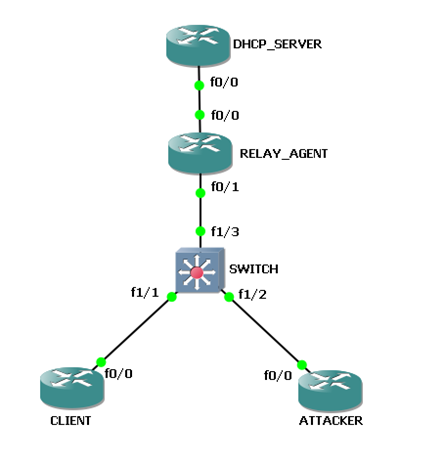
At times, a malicious user may attempt to install a rogue DHCP server on the network in the hope that potential client devices become victims. We need to remember a few things about the DHCP server: it provides the IP address, subnet mask, default gateway, and DNS server configurations to clients. The default gateway is used to forward traffic destined for a network outside of the LAN, and the DNS server resolves hostnames and IP address. What if the clients are using another default gateway and/or a compromised DNS server with false DNS entries? The following table shows the switches and the classification of ports as trusted/untrusted:
Switches | Ports |
| Trusted port |
| Untrusted port |
| Untrusted port |
When the DHCP snooping features are configured on a Cisco switch, it immediately converts all ports to become untrusted ports. An untrusted port prevents any DHCP Offer and DHCP ACK messages from entering the switch port. However, the port that the DHCP server is connected to must be manually configured as a trusted port:
DHCP trust zone
The following describes how the DHCP snooping feature actually functions:
- The DHCP snooping is enabled with the switch, the untrusted ports will forward only
DHCPDISCOVERandDHCPREQUESTpackets to the DHCP Server. The trusted port would only forwardDHCP OfferandDHCP Ackpackets back to the DHCP client.
Note
The DHCP server must be connected to a trusted port on the switch.
- When the attacker sends multiple fake
DHCPDISCOVERmessages to the server, the CPU utilization of the DHCP server goes up, and at some point the server will be out of IP addresses for that particular network in its pool. To avoid this, the DHCP snooping feature rate limits the DHCP traffic from trusted and untrusted sources so that only oneDHCPDISCOVERmessage can be sent by the client. - If any untrusted port exceeds the number of
DHCPREQUESTmessages, the port goes into anerr-disabledstate. - When DHCP snooping is enabled and configured, the switch maintains a DHCP snooping database that is used to keep track of untrusted sources, their leased IP address, and all the other TCP/IP settings.
- DHCP snooping can also be enabled for a particular VLAN of the switch interface. By default, it is disabled on all the VLAN interfaces.
A DoS attack is a process by which an attacker tries to create a disturbance in the network by triggering unwanted traffic, and this disables the network. The objective of this attack is to not allow network services to be available to legitimate users.
DoS attacks look legitimate, but the size of the traffic might increase to a level that cannot be managed by the victim, for example:
- Ping of Death (PoD): Sending continuous ICMP messages that cause the victim to crash or be unable to respond to legitimate requests
- TCP SYN flood: Simply creating a half-open TCP session on the victim server, thereby halting the services offered by the victim
Ping of Death
The Internet Control Message Protocol (ICMP) can be used to check basic network connectivity between two devices. Attacks can manipulate the size of the ICMP message to be greater than the normal size. A simple utility that uses the ICMP is known as ping.
If an attacker sends a ping of 65,536 bytes or greater to another device on a network, it will cause the recipient machine (victim) to crash. This type of attack is known as Ping of Death.
Let's take a look at the following diagram to better understand what takes place:
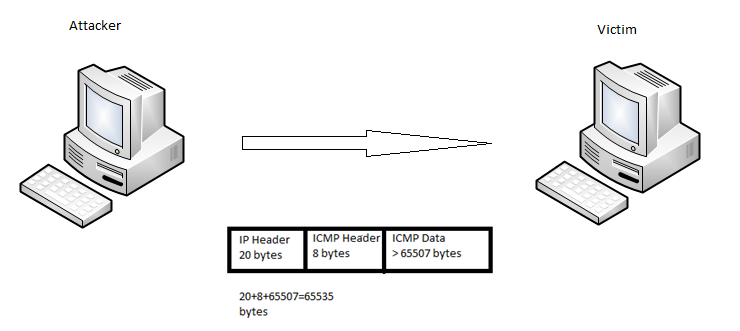
In this diagram, the victim that receives the fragmented packets will do the reassembly only to find that the final packet is greater than 65,536 bytes. Not knowing what to do with the packet, the system crashes or malfunctions, resulting in its inability to provide service to the legitimate users.
TCP SYN flood attacks
In most instances, whenever two devices want to communicate, they use the TCP protocol to ensure the message reaches both devices. The first process is known as the TCP three-way handshake. Once the handshake is completed, then data is allowed to flow between both devices. In a TCP SYN flood attack, the attacker sends a constant stream of SYN packets to the victim:
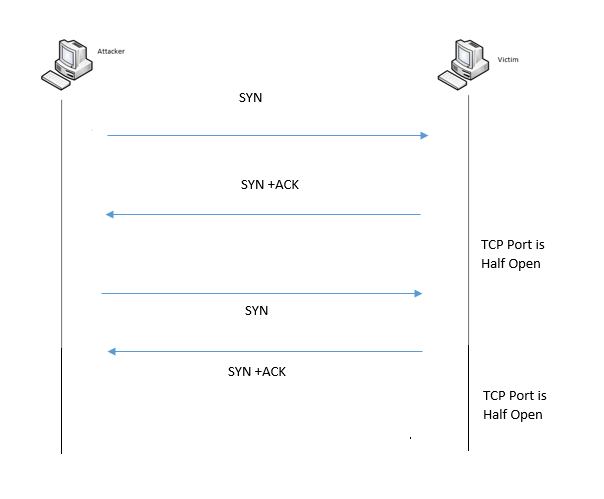
On the victim's end, for every SYN packet received, it must reply with an SYN/ACK packet. The attacker would receive this SYN/ACK packet but would not respond to it, therefore creating a lot of half-open connections on the victim machine. Remember, the attacker is continuously sending TCP SYN packets, which would eventually cause the victim's machine to exhaust its resources and not be able to create any future connections with other devices as long as the attack continues.
Password attacks
In a password attack, the attacker tries to obtain the password of a user account, an encrypted file, or even a network. The purpose can vary based on the attacker's intent. In doing so, there are a variety of different methods for attempting to gain the password of another person:
- Brute force attack: In a brute force attack, every possible combination of characters is attempted against the protected data until the correct combination is found. A brute force attack has the highest possibility of cracking the password; however, the downside is the length of time it may take before the password is found.
- Dictionary attack: This attack uses a password list to reference when attempting to crack the password. This attack may not always be a good choice since the success of the attack is only as good as the words that are in the actual wordlist of the password file.
- Keylogger: A keylogger can be either software- or hardware-based. The primary purpose of a keylogger is to capture keystrokes. This can be useful in capturing an unsuspecting user's password for a secure website, such as their online banking user account information.
- Trojan Horse: A Trojan Horse is a type of malware that disguises itself to look like a trusted program/software to trick its potential victims into installing it. Once installed, the actual malicious payload installs itself in the background and stays hidden from the victim. The payload can also be a software keylogger configured to send logs of data remotely back the attacker.
The main concept behind this attack is the weakness of the human mind in creating a strong password which contains alphanumeric characters, upper and lower cases with number(s) and a special character. This is sometimes an amateur way of obtaining critical information from users, such as bank account details, credit card PIN, or other confidential data. As a prerequisite, the attacker tries to look legitimate and provides information that looks real from a victim's perspective.
Different types of social engineering attacks can be seen:
- Phishing: This attack uses email as the mechanism through which an attacker disguised as a legitimate organization tries to get critical details, such as banking passwords.
- Vishing: This attack uses phones, through which the attacker tries to converse like a person from a legitimate organization and get critical details from the victim.
- Spear phishing: This attack is similar to phishing, but it focuses on a particular target from whom the attacker will steal information. It is important to note that the attacker gathers some information about the particular victim prior to launching this attack so that it looks like a particular email sent to the victim is legitimate, for example, targeting the CEO of an organization.
- Pharming: This is an attack where a rogue DNS server provides the wrong DNS IP for a particular URL, which leads the victim to a malicious site. Also, this can be done by injecting some incorrect DNS mappings into the host file on the Windows machine.
- Smishing: This attack uses SMS instead of email.
Buffer overflow attacks
In programming, a buffer is an area that is used to store data temporarily during program execution. The size of the buffer is usually fixed. Once the program closes, the contents of the buffer are also cleared. In a buffer overflow attack, the buffer is filled with more data than it can handle, causing the program to behave abnormally. Attackers use this attack to gain reverse shells into a victim machine by injecting shellcode as the payload.
Malware
Malware is any malicious software that can cause harm to any computing system or network. A piece of malware may have multiple functions, such as wiping data from a hard drive, capturing screenshots of the victim's monitor, or even creating a backdoor.
Some types of malware include:
- Viruses
- Crypto-malware, ransomware
- Worms
- Trojan Horse
- Rootkit
- Keylogger
- Adware/spyware
- Botnet
Network security tools
A tool is only as good as its wielder. There are many network security tool out there; some categories include tools for reconnaissance to help gather information on DNS, email addresses, and SNMP. At our fingertips, there's Nmap (Network Mapper), https://nmap.org, for exploitation development; the famous Metasploit from Rapid 7 (https://www.rapid7.com/products/metasploit/), for sniffing; Wireshark (https://www.wireshark.org/); and most importantly, one of the most advanced penetration platforms, Kali Linux (https://www.kali.org/) from Offensive Security.
We always need to remember hackers, network administrators, and cyber security professionals use network tools for different purposes. A white-hat hacker may use it to find vulnerabilities on a network before the black-hat hacker finds and exploits them. A penetration tester is trying to find and exploit any weakness in a network because it's their job.
Wireshark
Wireshark is referred to as the best protocol analyzer/sniffer. It has the ability to display all the Protocol Data Units (PDUs) for the four layers of the TCP/IP stack. Wireshark is a free tool for both Windows and Linux operating systems. It has the ability to see all the conversations/network traffic passing along a network segment:
To start a capture on Wireshark, simply open it and click on Capture | Options, then select the interface you want to capture traffic on. Now, click on Start.
Note
Wireshark can be found at https://www.wireshark.org/.
Metasploit
Metasploit is an exploitation development framework. This is a free tool for students and people who want to learn hacking in an ethical manner. The tool can be used with both Windows and Linux:
This is the Command Prompt from which Metasploit can be used. The console is referred to as msf.
Kali Linux
Kali Linux is a penetration testing Linux distribution. It was created by Offensive Security as the successor to the famous BackTrack. Kali Linux is a single operating system with all the possible tools and utilities needed for conducting a penetration test and forensics.
The amazing benefit of this distro is that it can be installed on a virtual machine, on a hard drive, it can be live-booted via USB, and can be installed on mobile devices, such as the Google Nexus, OnePlus smartphones, and the Raspberry Pi computer.
There are many categories of tools, such as information-gathering, scanners, password-cracking, exploitation development, post-exploitation, and forensics. The possibilities with Kali Linux are endless.





































































