In this section, we will look at how to dump the unpacked malware in memory to disk and fix its import table. In addition to this, if the import table has already been populated with API addresses by the loader, we will need to restore the original values. In this case, other tools will be able to read it, and we will be able to execute it for dynamic analysis.
Dumping the unpacked sample and fixing the import table
Dumping the process
To dump the process, you can use OllyDump. OllyDump is an OllyDbg plugin that can dump the process back to an executable file. It unloads the PE file back from memory into the necessary file format:
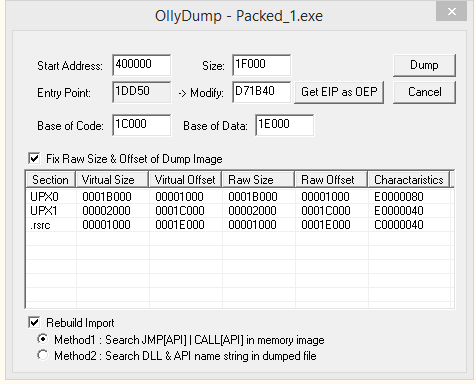
Figure 16: OllyDump UI
Once you reach the OEP from the previous manual unpacking process, you can set...





































































