Before we dive into the malicious activities of rootkits, let's take a look at how the Windows OS actually works and how the interaction between the user mode and kernel mode is organized. This knowledge will allow us to better understand the specifics of kernel-mode malware and what parts on the system it may target.
Windows internals
The infrastructure of Windows
As we mentioned previously, the OS is divided into two parts: user mode and kernel mode. This is demonstrated in the following diagram:
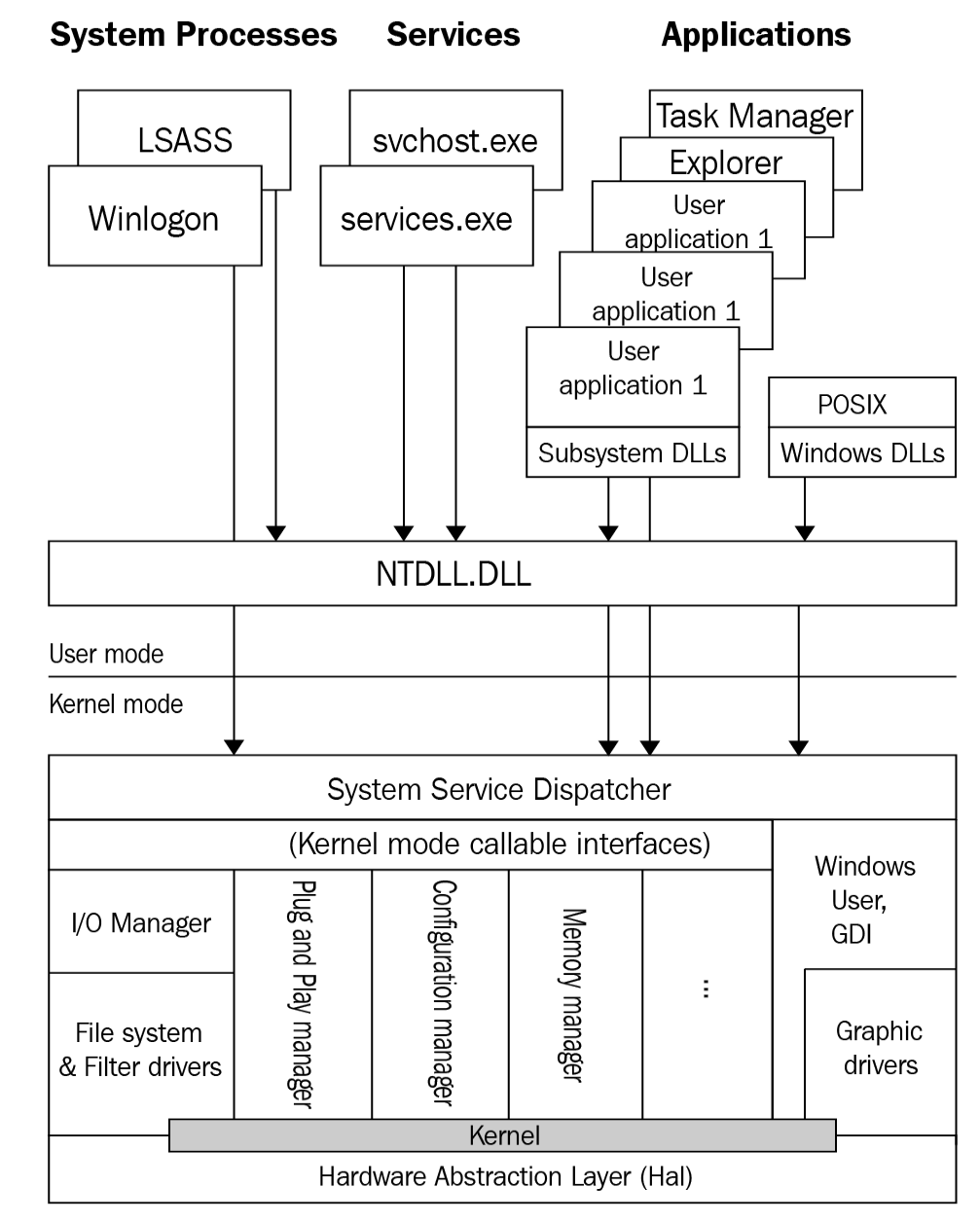
Figure 2: The Windows OS design
Now, let's learn about the scope of these applications:
- User mode: This contains all the processes and services running in the system (which you can see in task manager). These processes are...





































































