User-Authentication Methods
There are a number of authentication systems in use today, but I’m going to focus on the ones you’re likely to be confronted with on the Network+ exam.
Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) is a system that links users to public keys and verifies a user’s identity by using a certificate authority (CA). Think of a CA as an online notary public—an organization that’s responsible for validating user IDs and issuing unique identifiers to confirmed individuals to certify that their identity can really be trusted. Figure 13.12 shows how the CA process works in relation to two users.
Figure 13.12 The certificate authority process
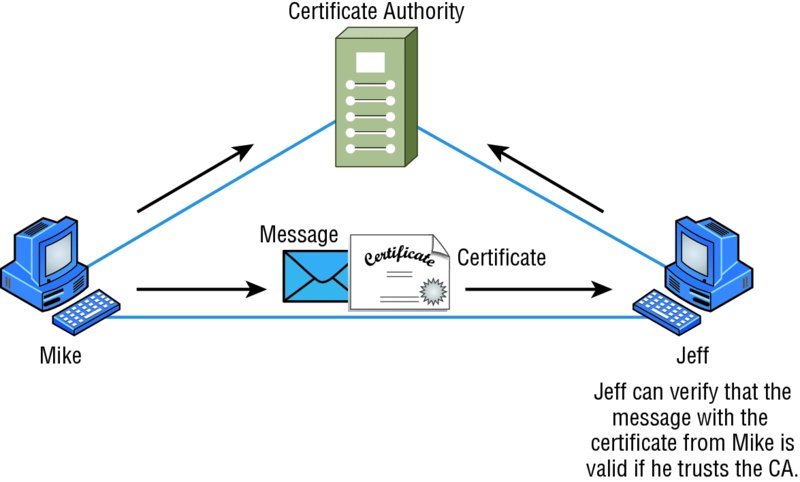
PKI allows people to communicate with each other with confidence that they’re talking to whom they think they are talking to. It is used to establish confidentiality and to ensure message integrity without knowing anything about the other party prior to the conversation...
























































