Intercepting the requests/responses using Burp Proxy
The Proxy tool is the heart of Burp. In summary, it intercepts all of the requests and responses that you try to manually visit using your browser. It operates as a web proxy server, and it sits as a man-in-the-middle between your browser and destination web servers. This lets you intercept, inspect, and modify the raw traffic passing in both directions (request/response):
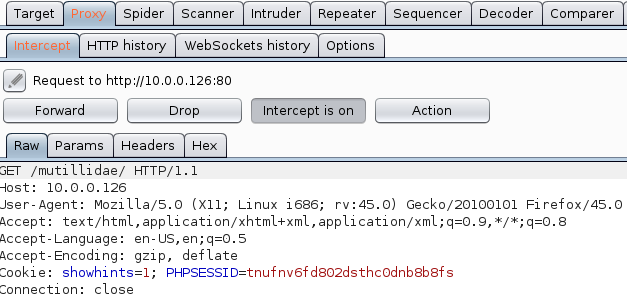
Setting the proxy in your browser
I'm assuming that you are using Kali Linux for your web application penetration testing, so you will be using Firefox or Iceweasel as a browser. You can install Chrome, but the instructions that I'm using are for Firefox (if you're using Chrome, don't worry; the settings should be very similar to Firefox).
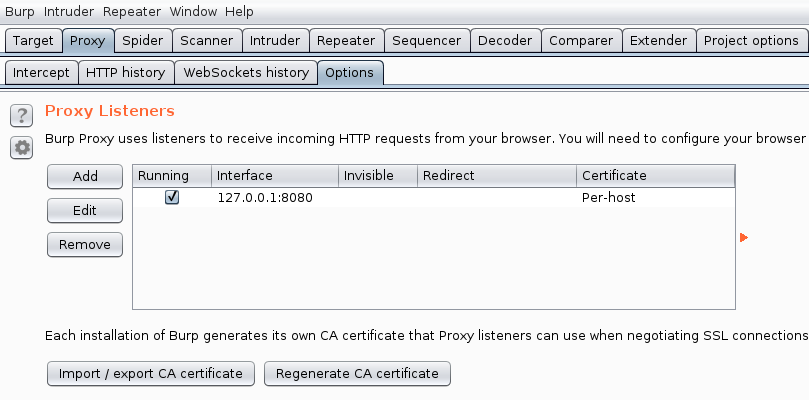
By default, Burp's port Proxy number is 8080, and this can be changed in the Options sub-tab under the Proxy tab:
Open Firefox and select Preferences from the menu. Click on the Advanced tab in the left menu; after that, select the Network...





































































