Maintaining access by using simple methods
In all of the examples that we've seen so far, we would lose our connection to the target computer as soon as the target user restarted the computer, because we used a normal backdoor, and once the computer restarted, that backdoor would be terminated, the process would be terminated, and we would lose our connection. In this section, we will discuss the methods that will allow us to maintain our access to the target computer, so that we can come back at any time and regain full control over the computer. There are a number of ways of doing this. The first one is by using Veil-Evasion; we can use an HTTP service or a TCP service instead of the HTTP backdoor that we created.
Let's look at an example. If we use Veil-Evasion and run the list command, we will see that at the numbers 6 and 8, we have service backdoors, as shown in the following screenshot:
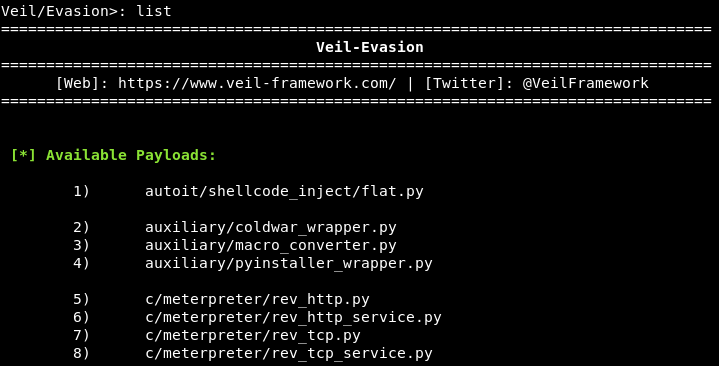
If we run use 6, all we have to do is set up the LHOST and then generate the backdoor; we can combine...





































































