Detecting ARP poisoning
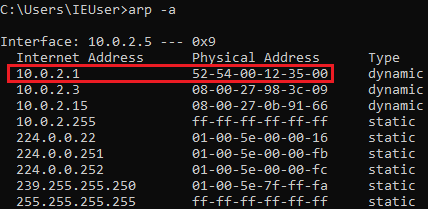
Let's take a look at how to detect ARP poisoning attacks. First of all, we need to gain an understanding of the ARP table. On our Windows device, which is the device that we always attack, we are going to run the arp -a command to list all the entries in the ARP table. Each computer has an ARP table, and that table associates IP addresses with MAC addresses. We have the IP address of a router, which is10.0.2.1 and is associated with the MAC address52-54-00-12-35-00, as shown in the following screenshot:
ARP poisoning works via trusted requests; as you can see in the previous screenshot, when a request is trusted, responses are accepted by the client even if a request isn't actually sent. The hacker sends a response to the client telling them that they are the router, which is automatically trusted and then accepted. Hacker will now send another response to the router, telling it that we're the client. This will modify the entries in the ARP tables for both the router...





































































