Detecting suspicious behavior
We will now look at how to use Wireshark to find suspicious activity within our network. Before we go any further, we need to change a few settings inside Wireshark; go to Edit | Preferences... under Protocols, find ARP/RARP and enable the option to Detect ARP request storms:
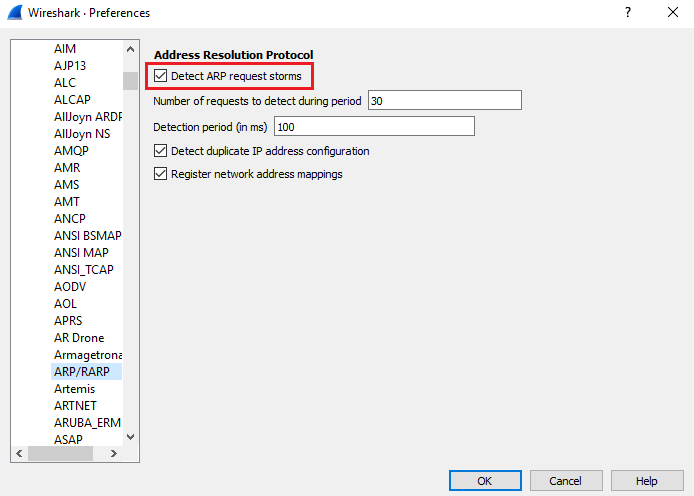
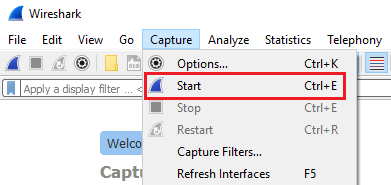
This will notify us if anybody is trying to discover any devices on the network. Click on OK and begin starting the capture by clicking on Capture | Start:
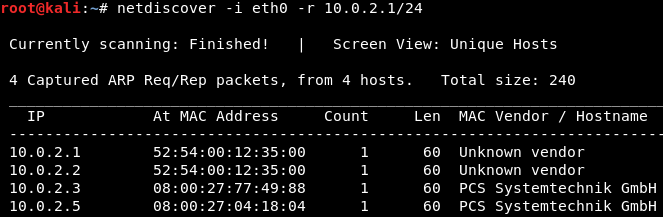
Now we need to switch to the Kali machine and use netdiscover. Instead of ARP poisoning, we are trying to discover what devices are connected to network. This is done by launching the following command:
netdiscover -i eth0 -r 10.0.2.1/24Once we have launched the netdiscover command, it quickly discovered the available devices on the network:
Wireshark will then generate packets that include the name of a device, what its destination is, and what it's inquiring from each IP address, as shown in the following screenshot:
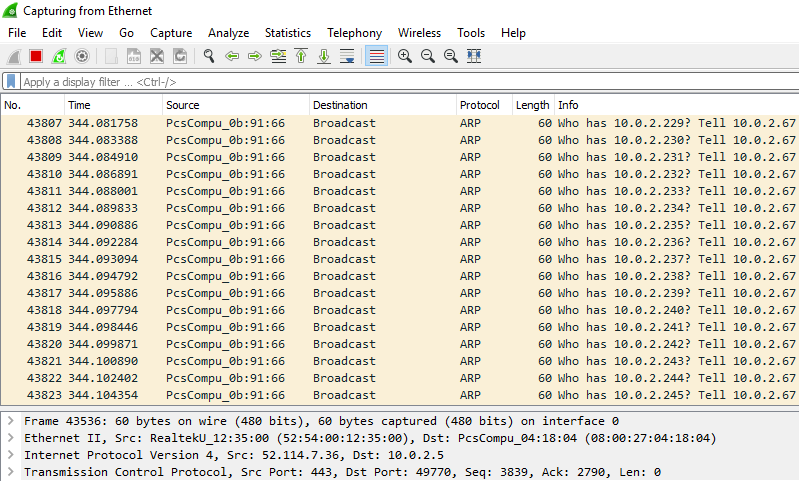
As the results show...





































































