Discovering an SQLi using the GET method
Now we will study an SQLi in a different file, on a different page, and see a few different things that we can do to exploit that vulnerability. So, first, go to the login page, which is in OWASP Top 10 | A1-Injection | SQL-Extract Data | User Info:
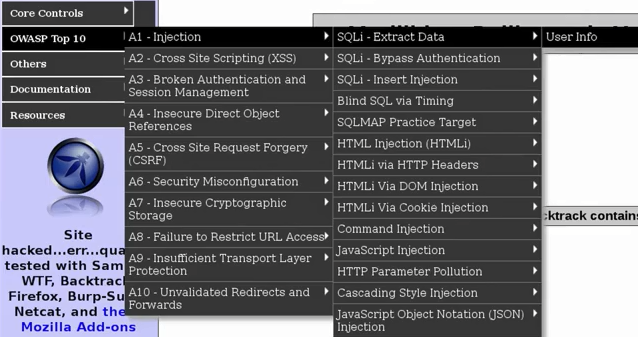
In the previous section, we went to the login page by clicking on the Login/Register option on the page; this time we're going to go through the User Info page, so the page will show us information about the user, provided we give the Name and Password. Enter all the credentials, such as username and password, and the page will show us all the username and password details and our signature, as shown:
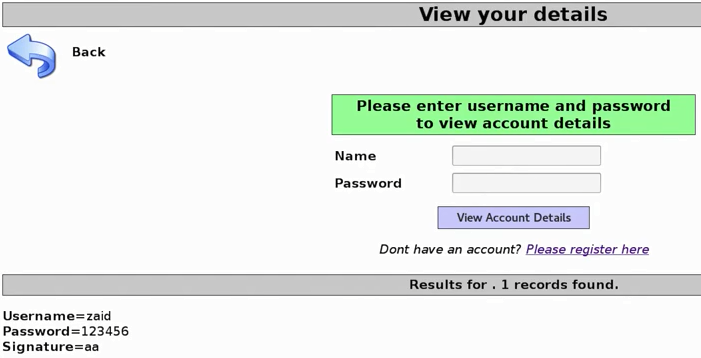
The statement that's been executed here is similar to what was executed when we logged in. As we can see in the following code, select * from accounts where $USERNAME is what we put in the username field, and $PASSWORD is what we put in the password field:
select * from accounts where username = '$USERNAME...




































































