Building a penetration testing laboratory
In the previous sections, we discovered the power of Docker containers and learned how to defend against Docker exploitation techniques. Let's move on to another aspect of Docker containers. In this section, you will learn how to build a penetration testing laboratory based on a Dockernized environment.
We started our learning process using Kali Linux distribution, so we will use the same distribution as a demonstration.
First, let's clone a Kali Linux container file from GitHub, using the git clone command:
git clone https://github.com/offensive-security/kali-linux-docker.git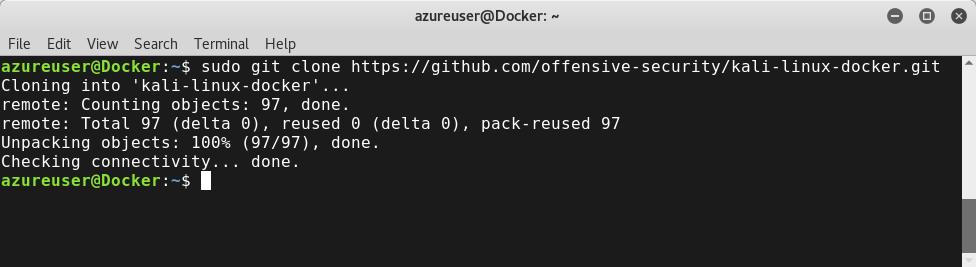
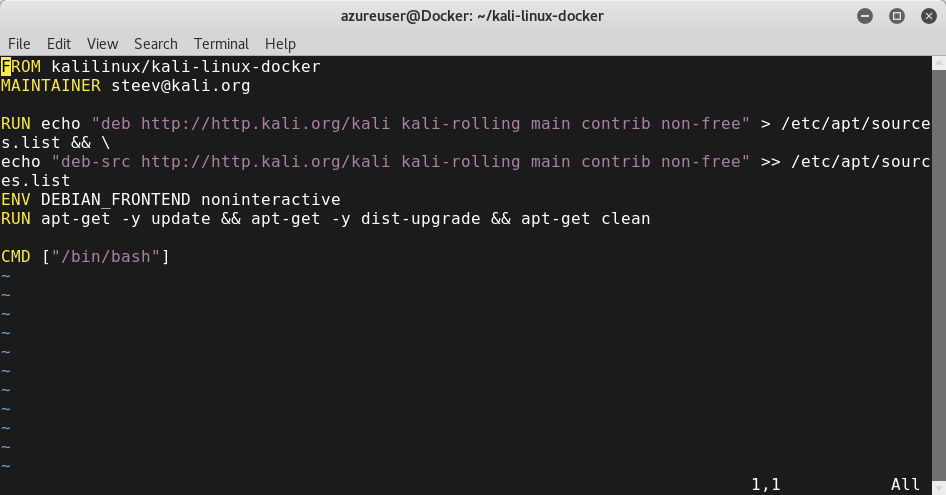
Open the Dockerfile and add any additional configuration:
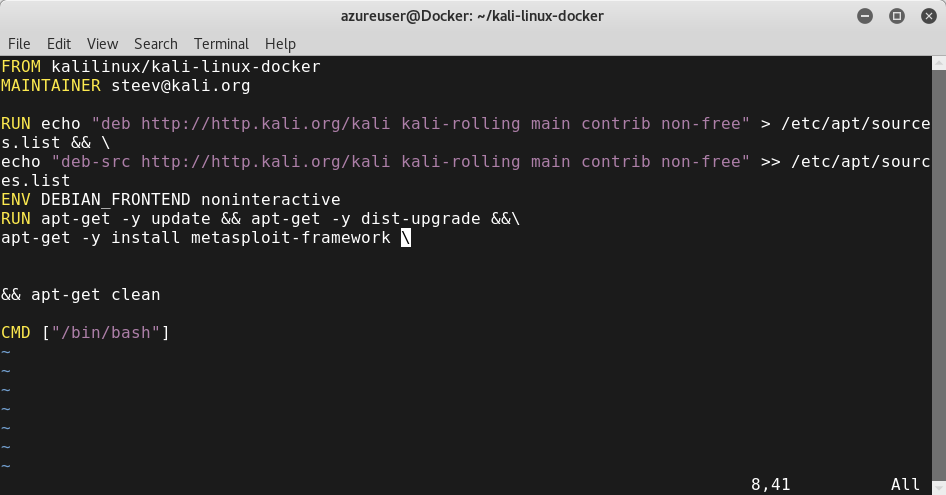
For example, I added metasploit-framework:
Now, let's build the image using the build command:
sudo docker build -t kali ~/kali-linux-docker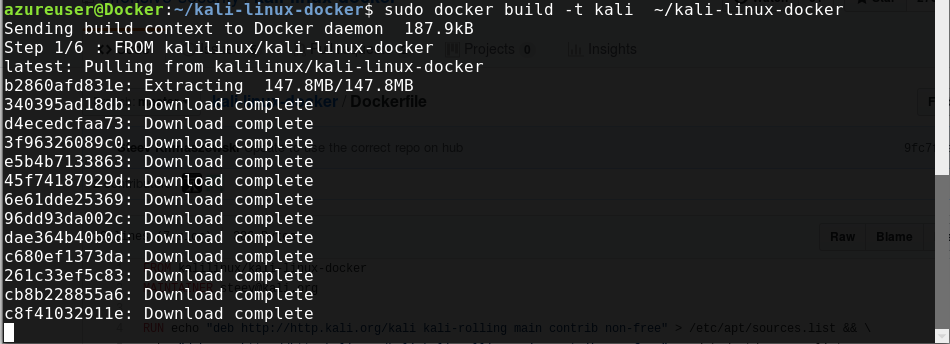
After completing the pull operation, the files will be extracted:
To keep data and make it persistent, make sure that you create an attached volume to Kali Linux to keep your files, even...





































































