Identifying and exploiting blind SQL injections
We already saw how an SQLi vulnerability works. In this recipe, we will cover a different vulnerability of the same kind, one that does not show an error message or a hint that could lead us to the exploitation. We will learn how to identify and exploit a blind SQLi.
How to do it...
Log into DVWA and go to SQL Injection (Blind):
- The form looks exactly the same as the SQLi form we saw in the previous recipes. Type
1in the textbox and clickSubmitto see the information about the user with the ID1.
- Now, let's perform our first test with
1'and see whether we get an error as in previous recipes:
We get no error message, but no result either. Something interesting could be happening here.
- We perform our second test with
1'':
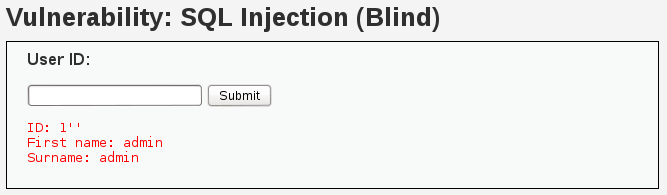
The result for ID 1 is shown. This means that the previous test (1') was an error that was captured and processed by the application. It's highly probable that we have an SQLi here, but it seems to be blind—no information about...





































































