Basic input validation bypass in Cross-Site Scripting attacks
One of the most common ways in which developers perform input validation is by blacklisting certain characters of words in information provided by users. The main drawback of this blacklisting approach is that elements that may be used in an attack are often missed because new vectors are found every day.
In this recipe, we will illustrate some methods for bypassing a weak implementation of a blacklisting validation.
How to do it...
We will start with DVWA in our vulnerable VM and set the security level to medium. Also, set Burp Suite as proxy for the browser:
- First, let's take a look at how the vulnerable page behaves at this security level. As shown in the following screenshot, when attempting to inject script code, the script tags are removed from the output:
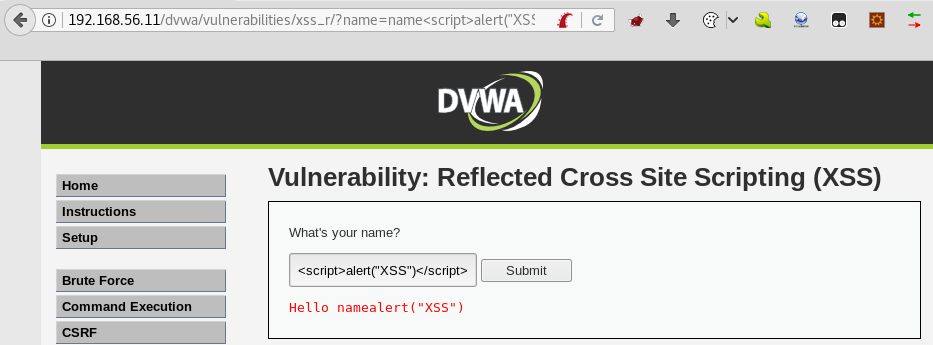
- Send that request to repeater and issue it again. As it can be seen in the next screenshot, the opening script tag is removed:
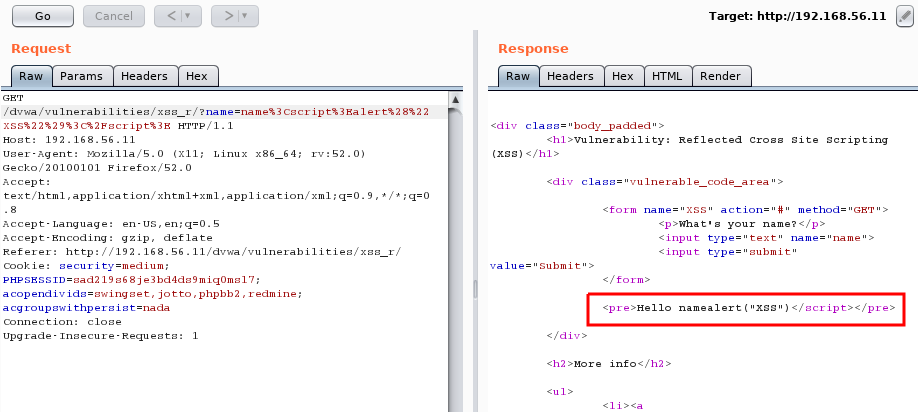
- There are multiple ways in which we can try to...





































































