Repeating requests with Burp Suite's repeater
When analyzing spider's results and testing possible inputs to forms, it may be useful to send different versions of the same request, changing specific values.
In this recipe, we will learn how to use Burp's Repeater to send requests multiple times with different values.
Getting ready
We begin this recipe from the point we left the previous one. It is necessary to have thevm_1virtual machine running, Burp Suite started in our Kali machine, and the browser properly configured to use it as a proxy.
How to do it...
For this recipe, we will use OWASP Bricks. The following are the steps required:
- Go to the first of the content exercises (
http://192.168.56.11/owaspbricks/content-1/). - In Burp Suite, go to
Proxy|History, locate aGETrequest that has anid=0orid=1at the end of the URL, right-click on it, and from the menu selectSend to Repeater:
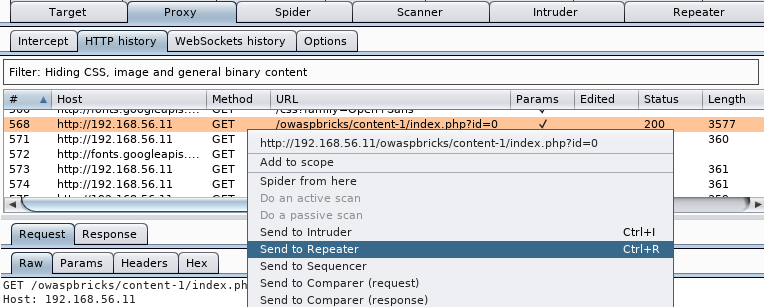
- Now we switch to the
Repeatertab.
- In
Repeater, we can see the original request on the left side. Let's click...





































































