Bypassing file upload restrictions
In previous chapters, we have seen how to avoid some restrictions in file uploads. In this recipe, we will face a more complete, although still insufficient, validation and chain another vulnerability in order to, first, upload a webshell into the server, and second, move it into a directory where we can execute it from.
How to do it...
For this recipe, we need Mutillidae II in our vulnerable VM to be at security level, use the Toggle Security option in the menu to set it, and use Burp Suite as proxy:
- In Mutillidae II's menu, go to
Others|Unrestricted File Upload|File Upload. - The first test will be to attempt uploading a PHP webshell. You can use the ones we used in previous chapters or make a new one. As follows, the upload will fail and we will receive a detailed description of why it failed:
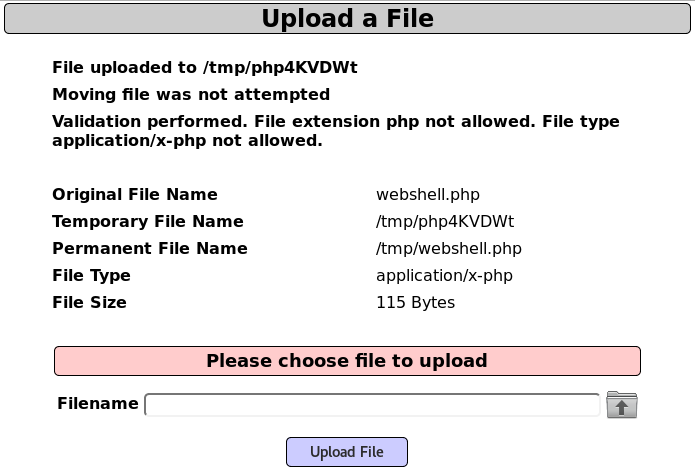
From the preceding response, we can infer that the files are uploaded to /tmp in the server, first using a randomly generated name, then file extension and type are...





































































