The detection of network anomalies
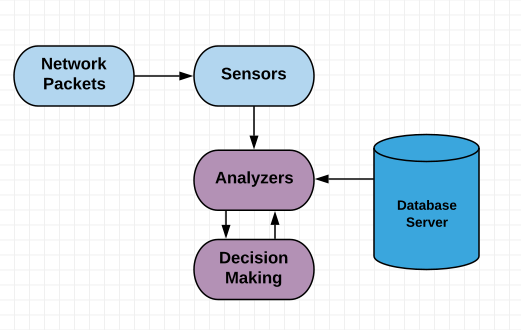
Network intrusion detection systems (IDSs) are not a new idea. They have been proposed since the earliest network attacks. IDS can be categorized into two major categories, based on their deployment: HIDS and NIDS. The following diagram illustrates a high-level overview of an IDS architecture:
HIDS
HIDS are able to collect and monitor computer systems (especially their internals) in order to give security analysts a deep visibility into what's happening on critical systems, such as workstations, servers, and mobile devices. The main goal of an HIDS is to detect intrusions.
NIDS
NIDS are responsible for detecting intrusions in network data. Basically, the detection is made based on specific patterns in sequential data. In other words, NIDSs read all of the incoming packets and try to find anomalies in them.
Anomaly-based IDS
When it comes to IDS, we are generally talking about two categories: host-based and network-based. But a new class of IDS has also arisen...



































































