Configuring and customizing Kali Linux
Kali is a framework that is used to complete a penetration test. However, the tester should never feel tied to the tools that have been installed by default or by the look and feel of the Kali desktop. By customizing Kali, a tester can increase the security of client data that is being collected, and make it easier to do a penetration test.
Common customizations made to Kali include these:
- Resetting the root password
- Adding a non-root user
- Speeding up Kali operations
- Sharing folders with MS Windows
- Creating encrypted folders
Resetting the root password
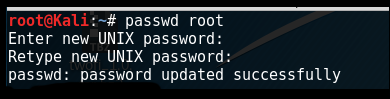
To change a user password, use the following command:
passwd rootYou will then be prompted to enter a new password, as shown in the following screenshot:
Adding a non-root user
Many of the applications provided in Kali must run with root-level privileges in order to function. Root-level privileges do possess a certain amount of risk, for example, miskeying a command or using the wrong command, which can cause applications to fail or even damage the system being tested. In some cases, it is preferable to test with user-level privileges. In fact, some applications force the use of lower-privilege accounts.
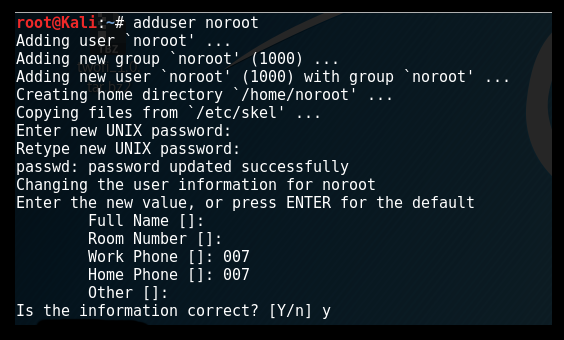
To create a non-root user, you can simply use the adduser command from the Terminal and follow the instructions that appear, as shown in the following screenshot:
Speeding up Kali operations
Several tools can be used to optimize and speed up Kali operations:
- When using a virtual machine, install the VM's software drive package: Guest Additions (VirtualBox) or VMware Tools (VMware). We need to ensure that we run
apt-get updatebefore the installation. - When creating a virtual machine, select a fixed disk size instead of the one that is dynamically allocated. It is faster to add files to a fixed disk, and there is less file fragmentation.
- The preload application (
apt-get install preload) identifies a user's most commonly used programs and preloads binaries and dependencies into memory to provide faster access. It works automatically after the first restart following installation.
- BleachBit (
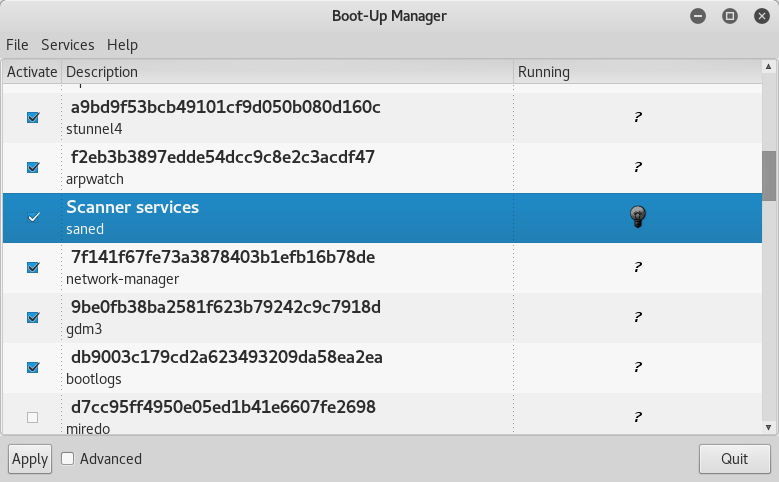
apt-get install bleachbit) frees disk space and improves privacy by freeing the cache, deleting cookies, clearing internet history, shredding temporary files, deleting logs, and discarding other unnecessary files. The advanced features include shredding files to prevent recovery and wiping free disk space to hide traces of files that have not been fully deleted. - By default, Kali does not show all applications that are present in the start-up menu. Each application that is installed during the boot-up process slows the system data and may impact memory use and system performance. Install Boot Up Manager (BUM) to disable unnecessary services and applications that are enabled during the boot up (
apt-get install bum), as shown in the following screenshot:
- Add
gnome-do(apt-get install gnome-do) to launch applications directly from the keyboard. To configuregnome-do, select it fromApplications|Accessories. Once launched, select thePreferencesmenu, activate theQuiet Launchfunction, and select a launch command (for example, Ctrl + Shift). Clear any existing commands and then enter the command line to be executed when the launch keys are selected. - Rather than launching directly from the keyboard, it is possible to write specific scripts that launch complex operations.
Sharing folders with the host operating system
The Kali toolset has the flexibility to share results with applications residing on different operating systems, especially Microsoft Windows. The most effective way to share data is to create a folder that is accessible from the host operating system as well as the Kali Linux VM guest.
When data is placed in a shared folder from either the host or the VM, it is immediately available via the shared folder to all systems that access that shared folder.
To create a shared folder, perform the following steps:
- Create a folder on the host operating system. In this example, it will be called
Kali_Share. - Right-click on the folder and select the
Sharingtab. From this menu, selectShare. - Ensure that the file is shared with
Everyoneand that thePermission Levelfor this share is set toRead / Write. - If you have not already done so, install the appropriate tools onto BackTrack. For example, when using VMWare, install the VMWare tools (refer to the Appendix, Installing Kali Linux).
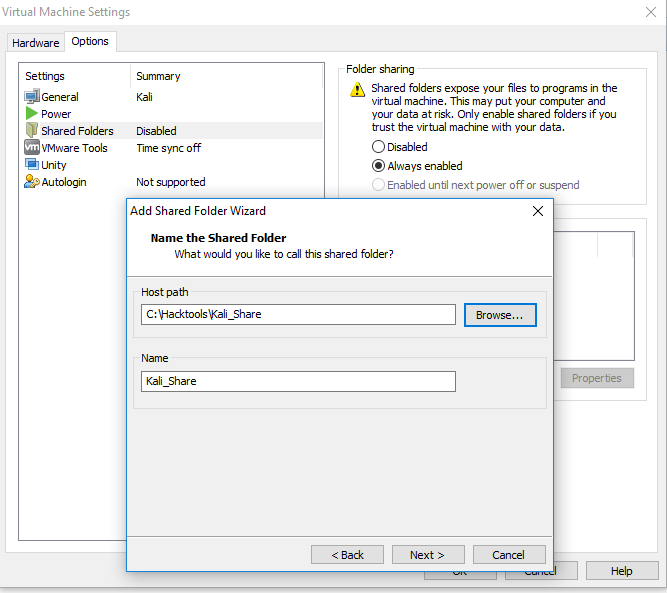
- When the installation is complete, go to the VMWare player menu, select
Manage, click onVirtual Machine Settings, locate the menu that enablesShared Folders, and selectAlways Enabled. Create a path to the shared folder that is present on the host operating system, as shown in the following screenshot:
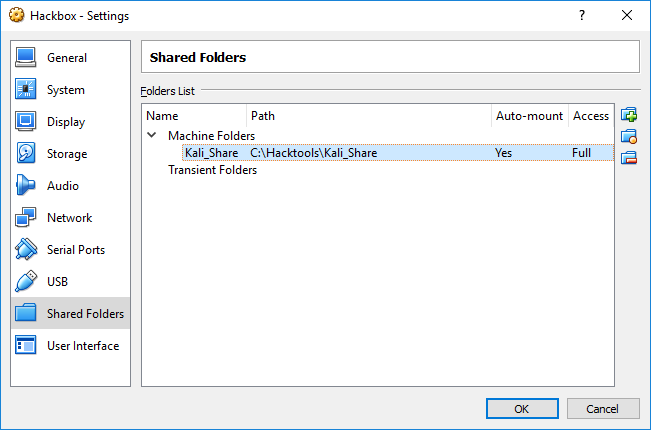
- In the case of Oracle VirtualBox, select the VM and go to
Settingsand selectShared Folders, as shown in the following screenshot:
Note
The older versions of VMware player use a different menu.
- Open the file browser on the Kali desktop. The shared folder will be visible in the
mntfolder (it might be placed in a subfolder,hgfs). - Drag the folder onto the Kali desktop to create a link to the real folder.
- Everything placed in the folder will be accessible in the folder of the same name on the host operating system, and vice versa.
The shared folder, which will contain sensitive data from a penetration test, must be encrypted to protect the client's network and reduce the tester's liability, should the data ever be lost or stolen.
Using BASH scripts to customize Kali
Typically, in order to maintain system and software development, command-line interfaces developed multiple shells in Linux, namely, sh, bash, csh, tcsh, and ksh.
We can utilize the following bash scripts to customize Kali Linux depending upon the goal of our penetration testing:
Building a verification lab
As a penetration tester, it is recommended that you set up your own verification lab to test any kind of vulnerabilities and have the right proof of concept before emulating the same on a live environment.
Setting up a virtual network with Active Directory
As we progress in building our own verification lab, the majority of the corporate companies utilize the Microsoft Active Directory for user administrative management and resource sharing such as printers, files, and identity management. Attackers are no longer interested in just running the command on the server or shutting it down, they are now more focused on owning a full domain controller that can potentially be the DNA of a company. We will perform some advanced attacks on Active Directory and the DNS server. In this section, we will install Active Directory on the Windows 2008 R2 server.
We will perform the same steps that we performed to install the Kali Linux to install Windows 2008 R2 to the same network.
Next, we will see step-by-step instructions to install Active Directory Domain Services. Assuming we have already installed the Microsoft Windows 2008 R2 server, click on Server manager, go to Roles, and then click on Add Roles. This should take us to Before you Begin and clicking on Next will bring up the following dialog box:
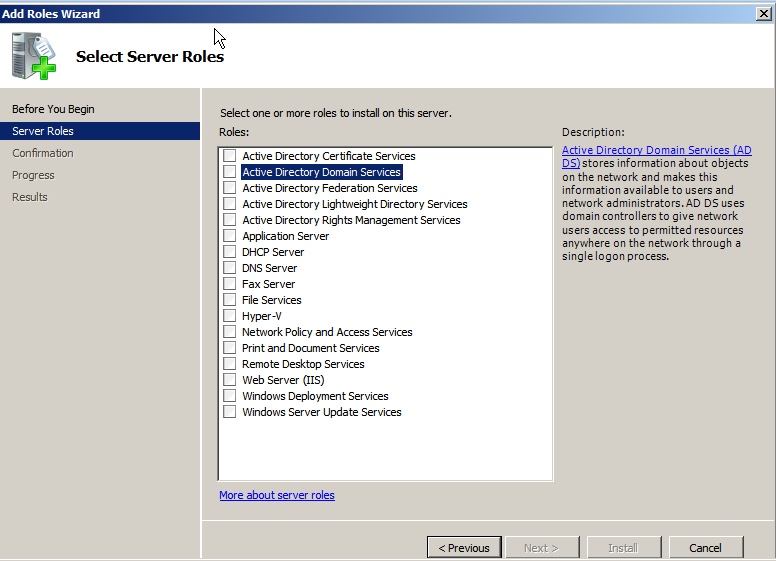
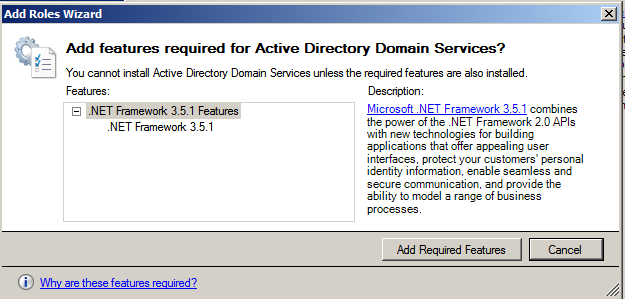
Select Active Directory Domain Services. When we select this, we are likely to get the following alert to install .Net framework 3.5.1 features, which is necessary to ensure all the API features are enabled. Click on Add Required Features, as shown in the following screenshot:
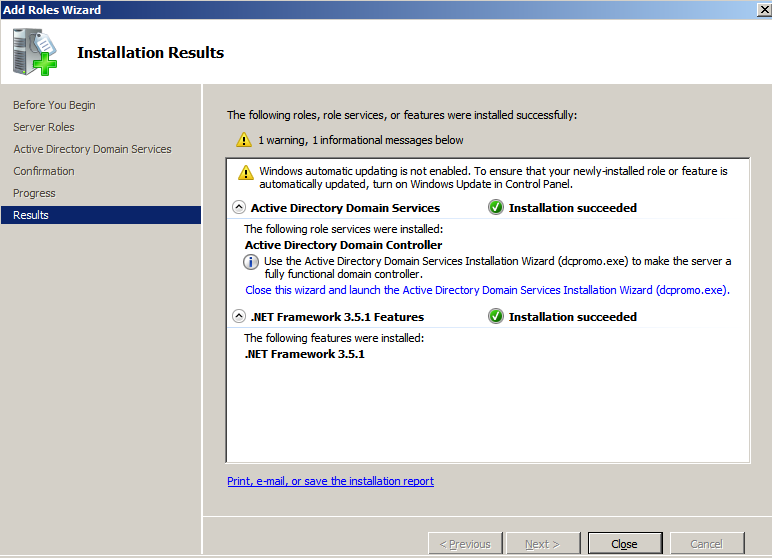
Let's move ahead and click on Install to continue. Both the items will be installed and we will see the successful completion of installation of AD Domain Services, as shown in the following screenshot:
Once the service is installed, we need to ensure that we run the service by clicking on the Active Directory Domain Services installation wizard and creating a new forest by following the instructions. In our case, we will be creating a new forest with FQDN as Secure.kali.com. Then with the Domain NetBIOS name as Secure, set the forest functional level to Windows 2003 or Windows 2008 R2. This will invoke DNS (Domain Name Server). As a fresh install, we will need to install DNS and follow the wizard and finally we must have a new domain as secure.kali.com, as shown in the following screenshot:
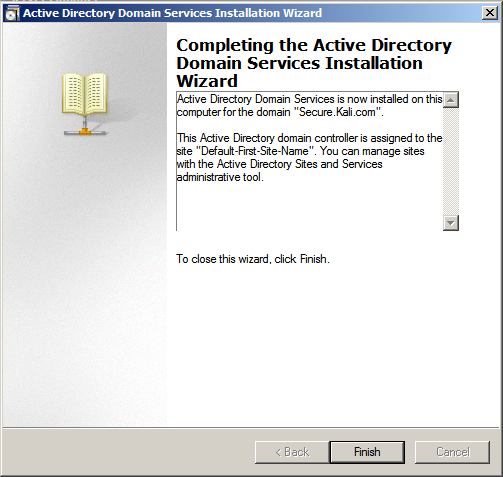
Installing defined targets
Practice makes a man perfect. In order to practice the art of exploitation, it is always recommended that you make use of the well-known vulnerable software. In this section, we will install metasploitable3, which is a Windows platform, and Multilladae, which is a PHP framework web application.
Metasploitable3
Metasploitable3 is an indubitable vulnerable virtual machine, which is intended to be tested for multiple exploits using metasploit. It is under BSD-style license. This virtual machine can be downloaded from https://github.com/rapid7/metasploitable3. You can download the ZIP file and unzip it to your favorite Windows location (typically, we segregate this in the c:\HackTools\ folder) or you can use the git clone link with the bash command.
Install all the relevant supporting software such as Packer, Vagrant, VirtualBox, and the Vagrant reload plugin.
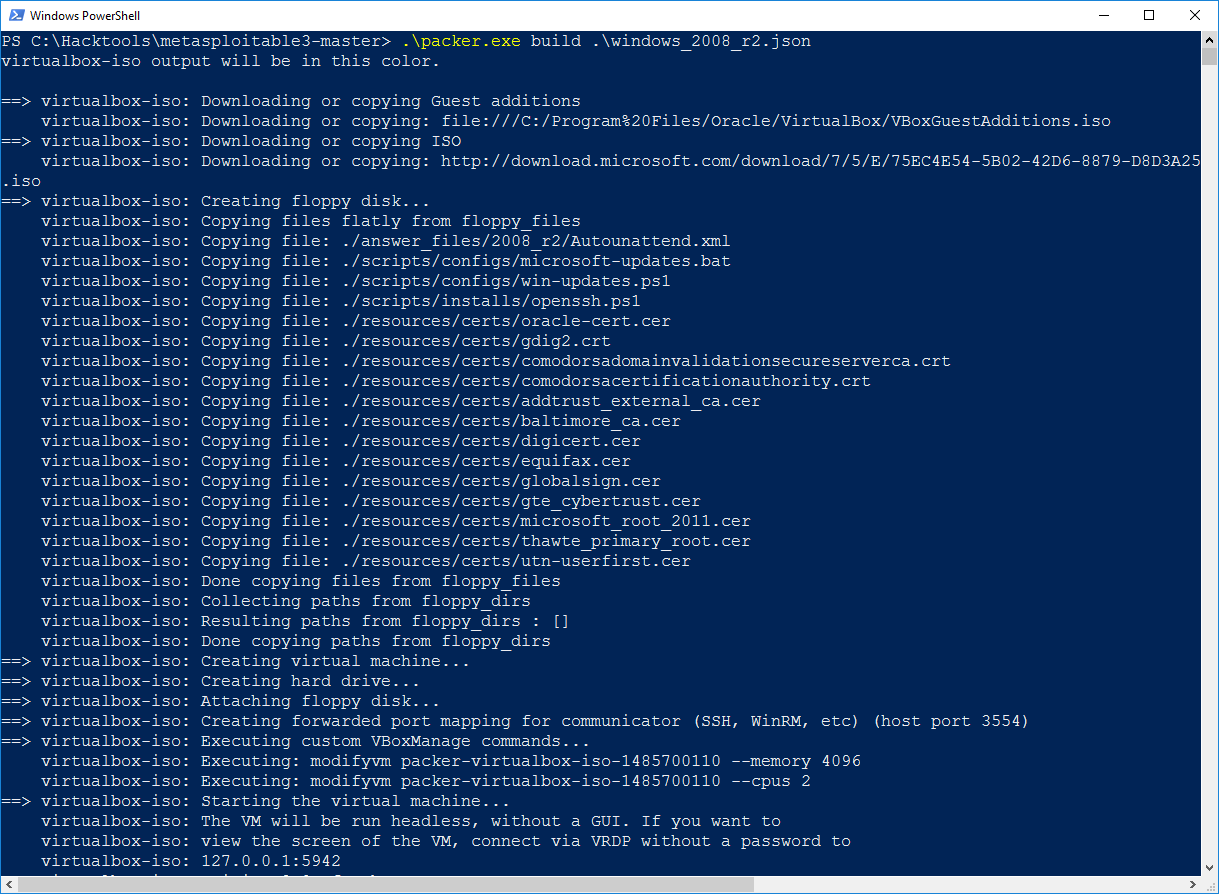
The following is a snapshot of the manual installation of Metasploitable3 on the Windows 10 host operating system:
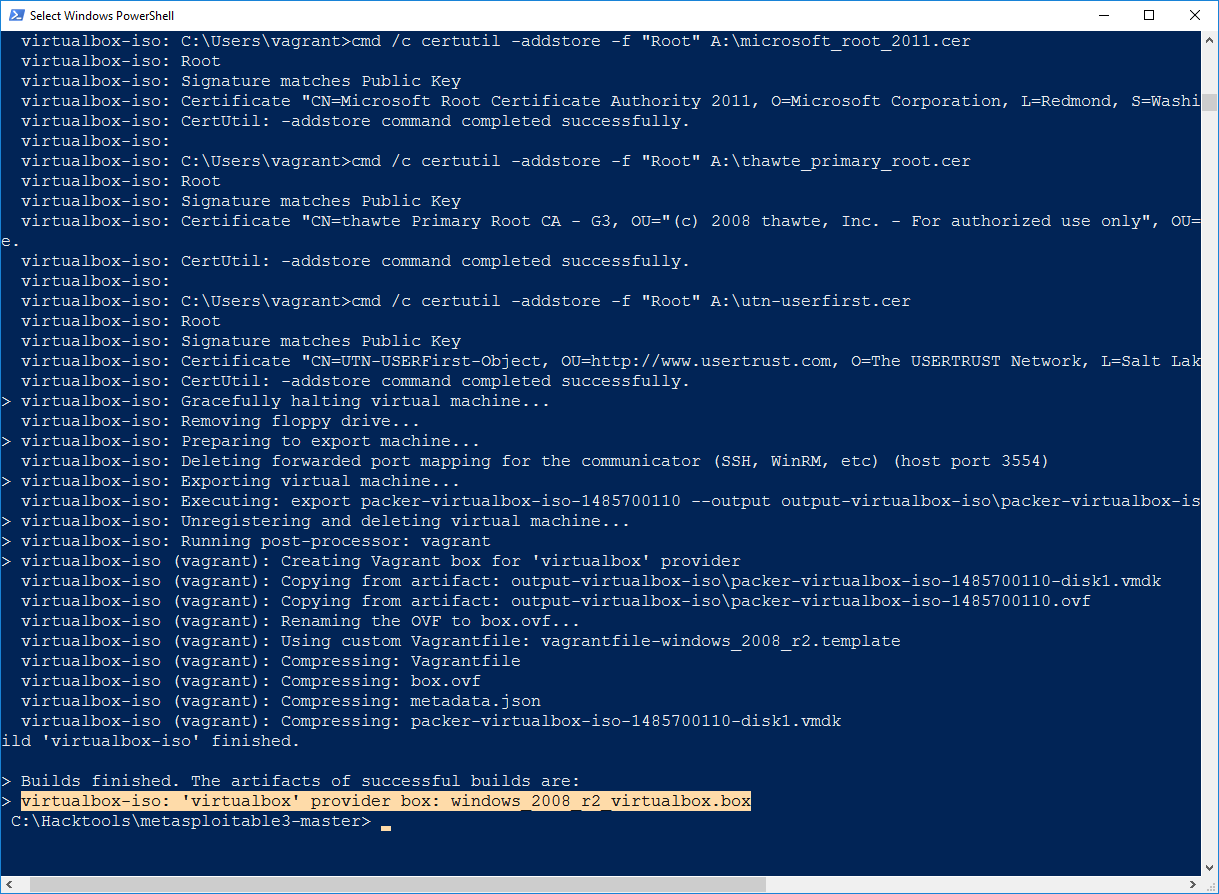
Once the packer build has downloaded the ISO vbox image, you will receive a message as shown in the following screenshot:
After the VirtualBox file is downloaded, you will just have to run vagrant up in the same PowerShell. This should bring up your new VM in your virtual box without any problem, as shown in the following screenshot:
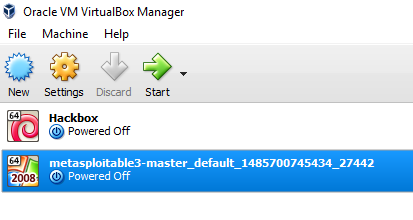
Mutillidae
Mutillidae is an open source insecure web application, which is designed for penetration testers to practice all the web app specific vulnerability exploitation.
XAMMP is another free and open source cross-platform web server solution stack package developed by Apache Friends. The XAMPP can be downloaded from this URL:https://www.apachefriends.org/download.html.
We will now be installing Mutillidae to our newly installed Microsoft Windows 2008 R2 server to host it. Once XAMMP is downloaded, let's go ahead and install the executable by following the wizard. Once the installation is complete, launch the XAMPP and you should be able to see the following screen:
Mutillidae can be downloaded from https://sourceforge.net/projects/mutillidae/files/latest/download.
Unzip the file and copy the folder to c:\yourxampplocation\htdocs\<mutillidae>.
We should be able to see the web application installed successfully, as shown in the following screenshot, and it can be accessed by visiting http://localhost/mutillidae/:
Managing collaborative penetration testing using Faraday
One of the most difficult aspects of penetration testing is remembering to test all of the relevant parts of the network or system target, or trying to remember if the target was actually tested, after the testing has been completed. In some cases, a single client may have multiple penetration testers performing scanning activities from multiple locations and the management would like to have a single view. Faraday can provide a single view assuming all the penetration testers are able to ping each other on the same network or on the internet for external assessment.
Faraday is a multiuser penetration test Integrated Development Environment (IDE). It is designed for testers to distribute, index, and analyze all the data that is generated during the process of a penetration testing or technical security audit to provide different views such as management, executive summary, and also an overall issues list.
This IDE platform is developed in Python by InfoByte. Download the application from the https://github.com/infobyte/faraday/wiki link or directly git clone the link, as shown in the following screenshot:
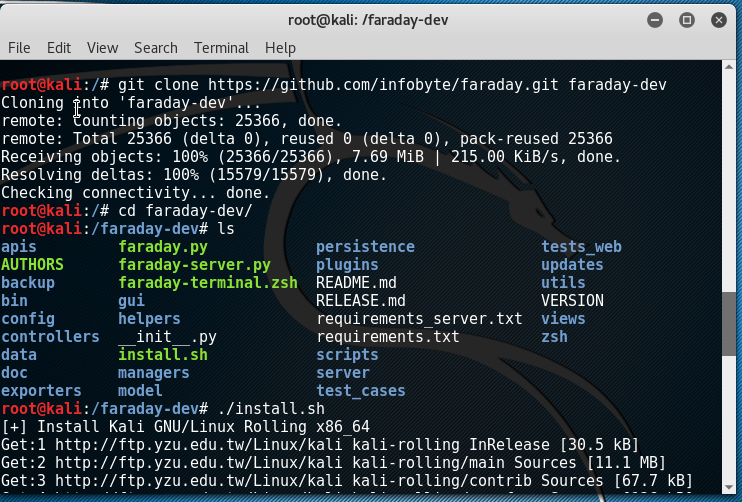
Once the folder is cloned to your Kali Linux, run ./install.sh to install any dependencies. Do not forget to start the CouchDB service as Faraday utilizes CouchDB as its database for storage. Finally, we run faraday-server.py to launch the Faraday server for an integrated platform, and then as the client, we should be able to launch Faraday by running faraday.py, as shown in the following screenshot:
Launching Faraday should open up the Faraday shell console to us, as shown in the following screenshot:
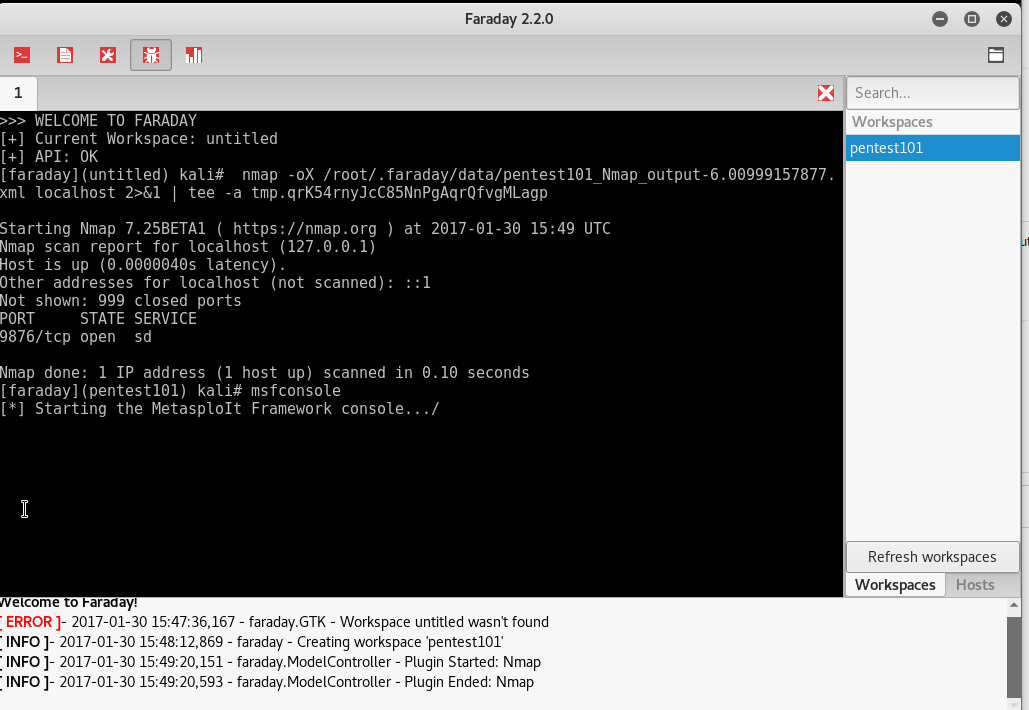
One positive aspect of the application is that any scanning you do, or any other penetration tester does, you will be able to visualize the information by clicking onfaraday web, as shown in the following screenshot:
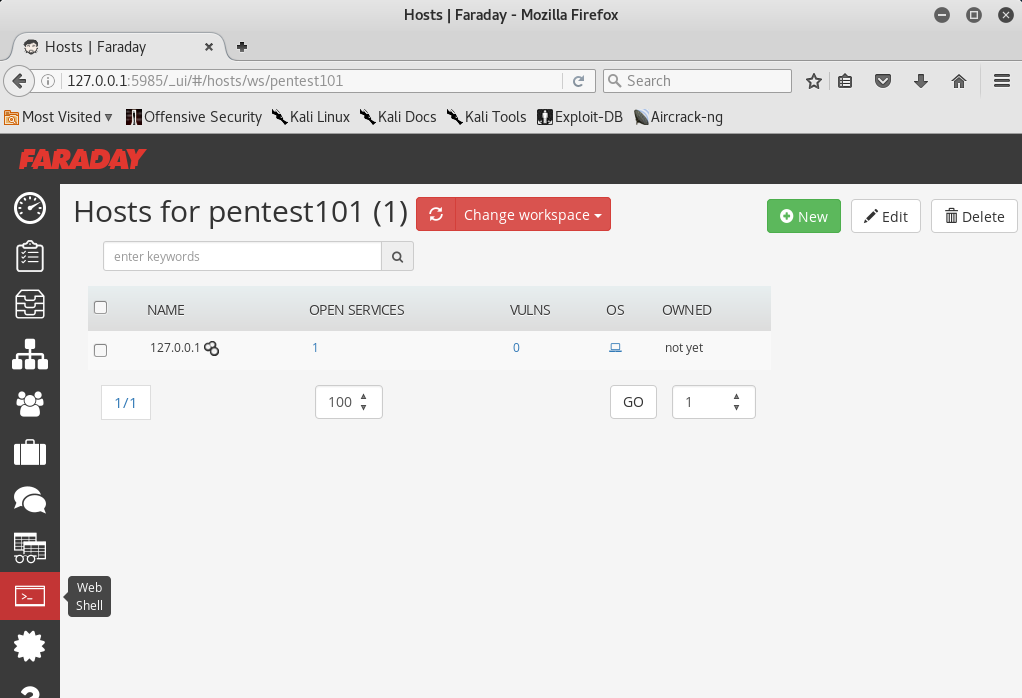
There is a limitation on the free version of Faraday for the community, which can be utilized to visualize all the lists of issues in a single place.






































































