Methodology and attack methods
As an attack route supporting the kill chain methodology, social engineering focuses on the different aspects of an attack that take advantage of a person's trust and innate helpfulness to deceive and manipulate them into compromising a network and its resources. The following diagram depicts the different types of attack methods that attackers can engage in to harvest information:
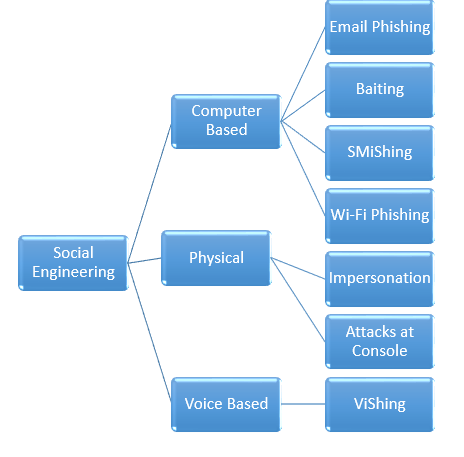
Social engineering involves three main categories: computer-based, voice-based, and physical attacks. The following sections will provide a brief on every type and we will explore the computer-based attacks in this chapter, especially physical attacks and email phishing, in particular using the Kali Linux.
Computer-based
Attacks that utilize computers to perform social engineering are subdivided into the following types. All these different types will be best utilized only when all the passive and active reconnaissance information is utilized to the maximum:
- Email phishing: Attackers...





































































