Installing Kali to the cloud – creating an AWS instance
AWS is a cloud-based platform from Amazon primarily built to offer customers the power of compute, storage, and content delivery anywhere and anytime. As a penetration tester or hacker can utilize AWS to conduct penetration testing, in this section, we will go through the easiest ways of installing Kali Linux into AWS, which will be handy in case of external command and control.
First, you will need to have a valid AWS account. You can sign up by visiting the following URL:https://console.aws.amazon.com/console/home
When we log in to the AWS account, we will be able to see all the AWS services, as shown in the following screenshot:
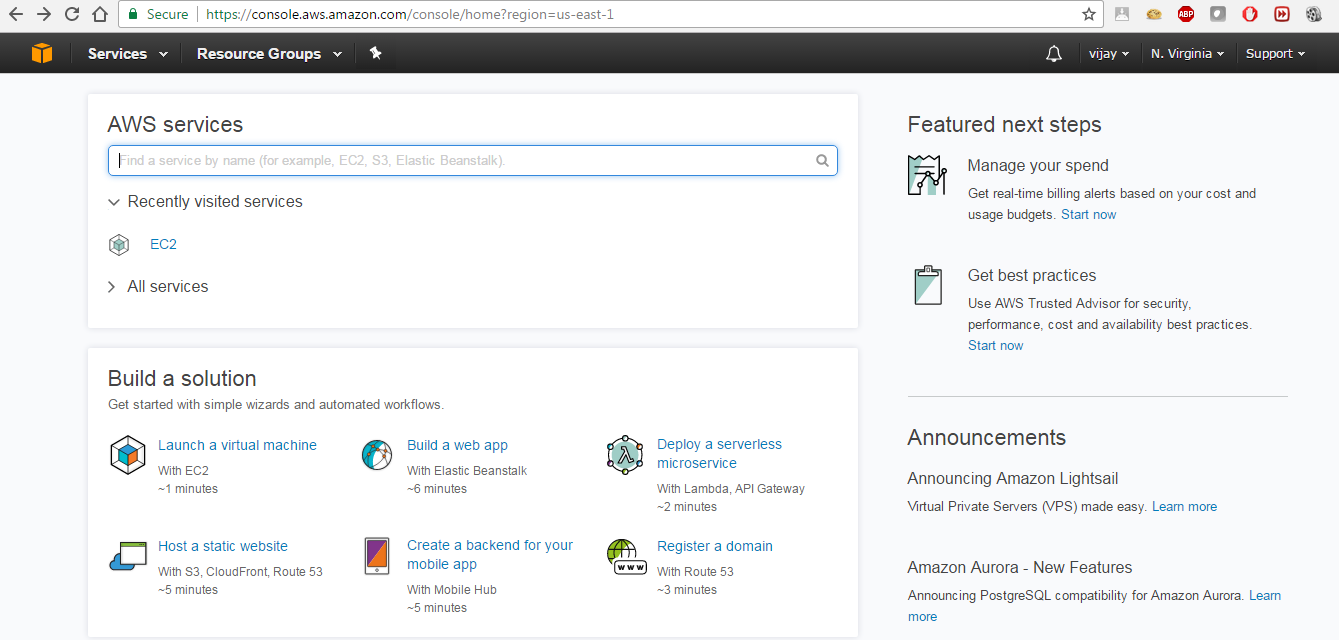
The second step is to launch Kali Linux on AWS as an instance. Rather, we will customize Kali Linux by installing a Debian operating system. The open source community has made it very simple to directly launch with preconfigured Kali Linux 2016.2 in the Amazon Marketplace. The following URL will enable us to directly launch Kali Linux within few minutes:
https://aws.amazon.com/marketplace/pp/B01M26MMTT
When you visit the link, you will be able to see something similar to the following screenshot:
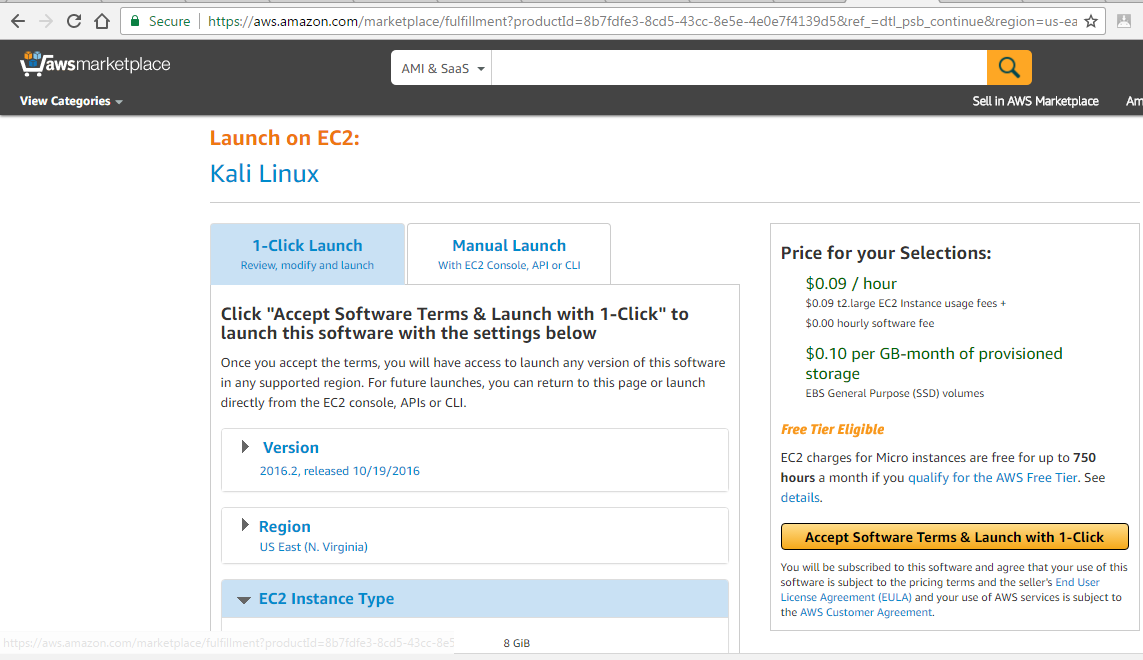
Click on the Accept Software Terms & Launch with 1-Click button and go to your AWS console by visiting https://console.aws.amazon.com/ec2/v2/home?region=us-east-1. You should now be able to launch the instance by clicking on Launch Instance by selecting the Instance ID or the row, as shown in the following screenshot:
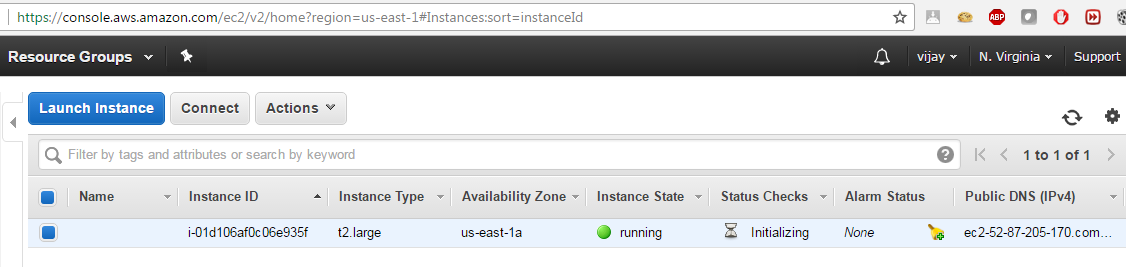
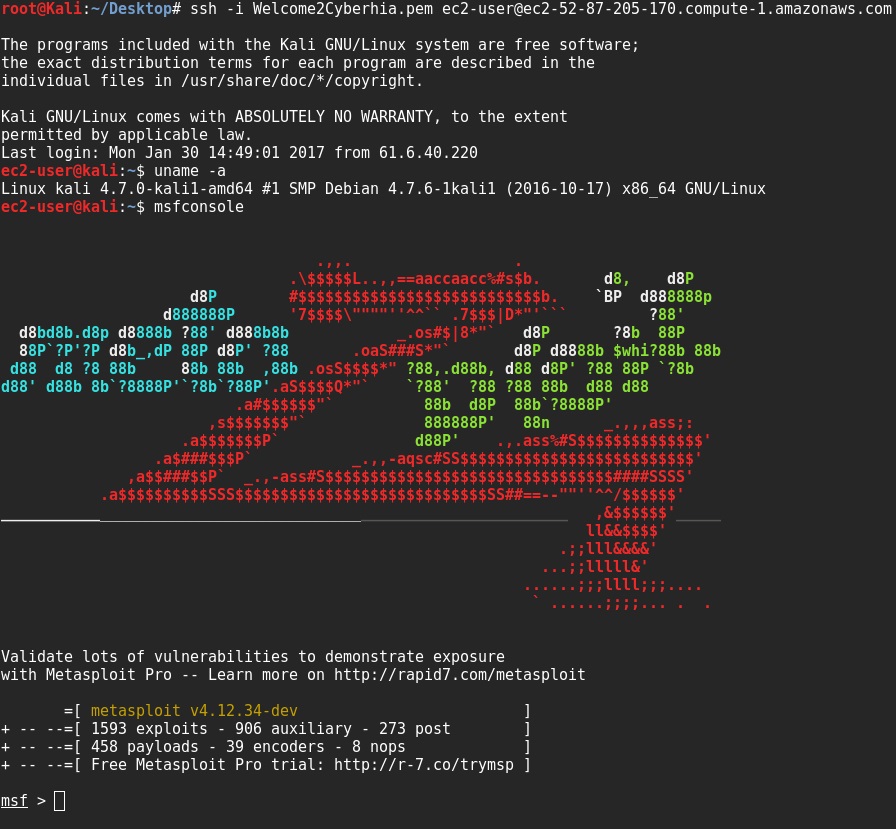
We will need to create a key-value pair in order to make sure only you can access Kali Linux. You will now be able to log in to your AWS cloud using your private key that you generated during the key-value pair. Then, you should be able to log in by entering the following command from your command shell:
ssh -i privatekey.pem ec2-user@amazon-dns-ipThe following screenshot depicts the successful installation of Kali on AWS:
All the terms and conditions must be met in order to utilize AWS to perform penetration testing. Legal terms and conditions must be met before launching any attacks from the cloud host.






































































