Writing your own port scanner using netcat
While attackers utilize the proxying application and Tor network, it is also possible to write their own custom network port scanner. The following one line command can be utilized during penetration testing to identify the list of open ports just by using netcat:
while read r; do nc -v -z $r 1-65535; done <iplist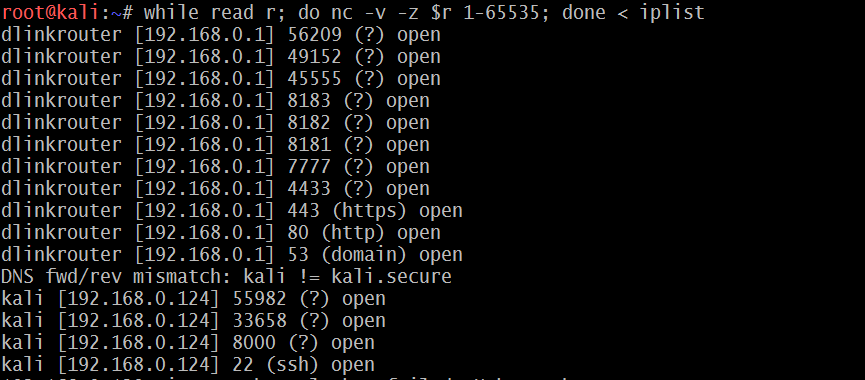
The same script can be modified for more targeted attacks on a single IP as follows:
while read r; do nc -v -z target $r; done < portsThe chances of getting alerted in any intrusion detection system using custom port scanners is high.
Fingerprinting the operating system
Determining the operating system of a remote system is conducted using two types of scans:
- Active fingerprinting: The attacker sends normal and malformed packets to the target and records its response pattern, referred to as the fingerprint. By comparing the fingerprint to a local database, the operating system can be determined.
- Passive fingerprinting: The attacker sniffs...





































































