Prepping up with custom tools
These tools you will install are open source available on GitHub. They are much faster and contain collections of different tweaks that people have included over a period of time during their own pentesting experience.
Getting ready
Here is a list of some tools that you will need before we dive deeper into penetration testing. Not to worry, you will be learning their usage with some real-life examples in the next few chapters. However, if you still wish to learn basics in an early stage it can simply be done with simple commands:
toolname -helptoolname -h
How to do it...
Some of the tools are listed in the following sections.
Dnscan
Dnscan is a Python tool that uses a wordlist to resolve valid subdomains. To learn about Dnscan follow the given steps:
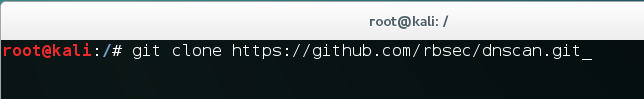
- We will use a simple command to clone the git repository:
git clone https://github.com/rbsec/dnscan.gitThe following screenshot shows the preceding command:
- You can also download and save it from https://github.com/rbsec/dnscan.
- Next we browse into the directory where we downloaded Dnscan.
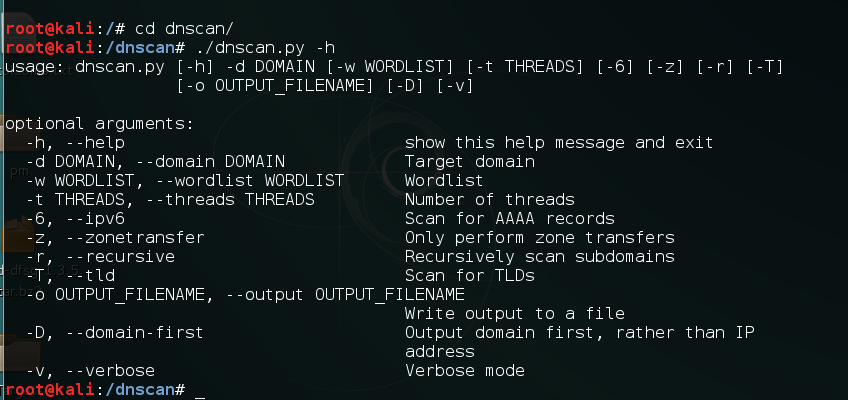
- Run Dnscan by using the following command:
./dnscan.py -hThe following screenshot shows the output for the preceding command:
Subbrute
Next we will install subbrute. It is amazingly fast and provides an extra layer of anonymity as it uses public resolvers to brute force the subdomains:
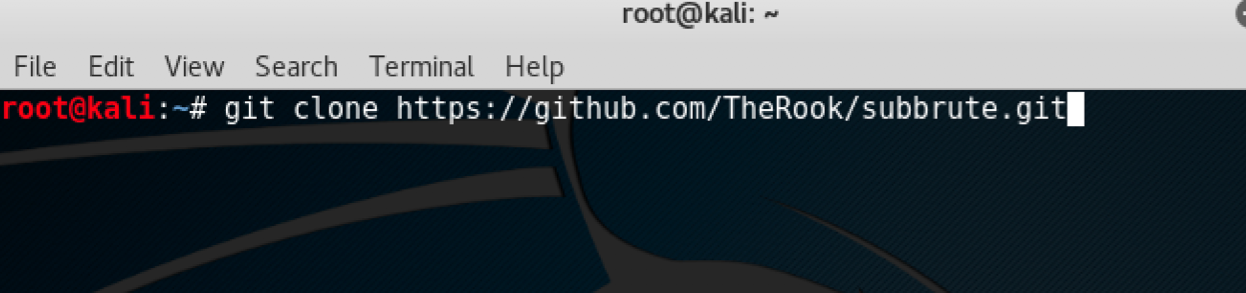
- The command here is again simple:
git clone https://github.com/TheRook/subbrute.gitThe following screenshot shows the preceding command:
- Or you can download and save it from https://github.com/TheRook/subbrute.
- Once the installation is complete we will need a wordlist for it to run for which we can download dnspop's list. This list can be used in the previous recipe too: https://github.com/bitquark/dnspop/tree/master/results.
- Once both are set up we browse into the subbrute's directory and run it using the following command:
./subbrute.py- To run it against a domain with our wordlist we use the following command:
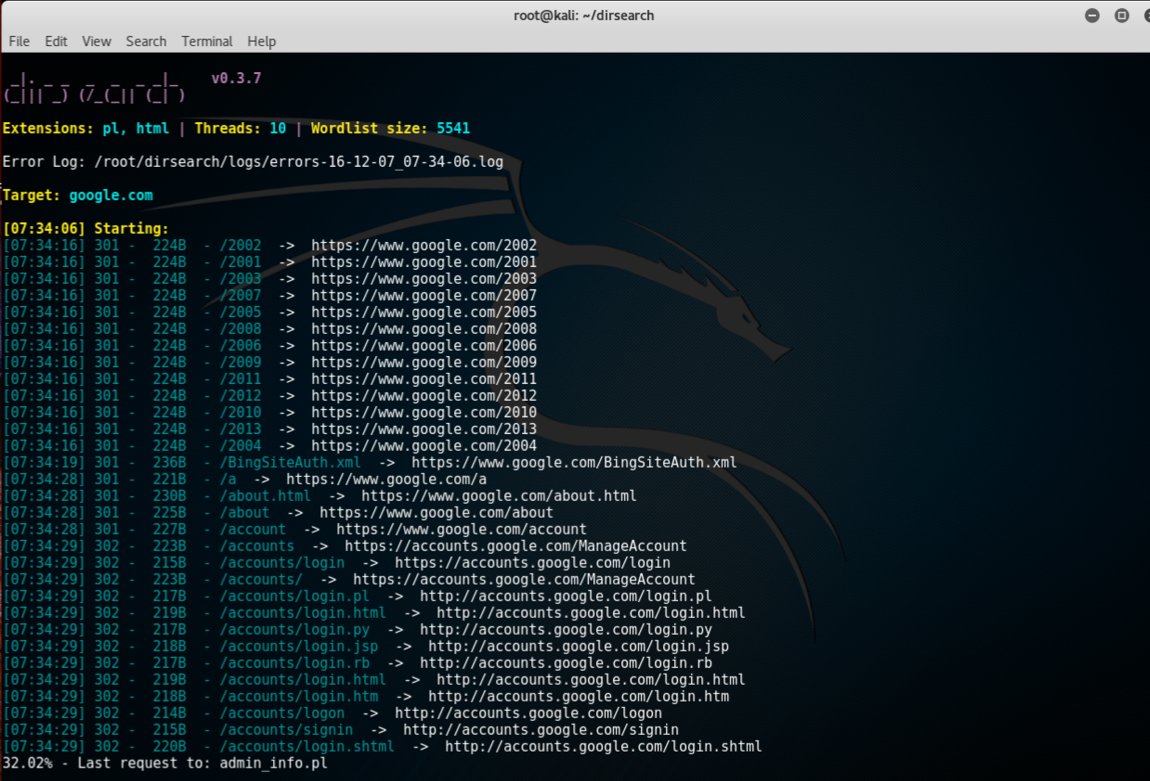
./subbrute.py -s /path/to/wordlist hostname.comDirsearch
Our next tool in the line is dirsearch. As the name suggests it is a simple command-line tool that can be used to brute force the directories. It is much faster than the traditional DIRB:
- The command to install is:
git clone https://github.com/maurosoria/dirsearch.git- Or you can download and save it from https://github.com/maurosoria/dirsearch. The following screenshot shows the preceding command:
- Once the cloning is complete browse to the directory and run the tool by using the following:
./dirsearch.py -u hostname.com -e aspx,phpThe following screenshot shows the output for the preceding command: