Cyber Threat Intelligence
Considering all the stated in the preface, we are going to define Cyber Threat Intelligence as a cybersecurity discipline that attempts to be a proactive measure of computer and network security, which nourishes itself from the traditional intelligence theory.
Cyber Threat Intelligence (CTI) focuses on data collection and information analysis to gain a better understanding of the threats facing an organization in order to protect its assets. The objective of a CTI analyst is to produce and deliver relevant, accurate and timely curated information, i.e. intelligence, so that the recipient organization can learn how to protect itself from a potential threat.
The sum of related data generates information, which through analysis, is transformed into intelligence. But, as we stated before, intelligence only has value if it is relevant, accurate and more important, if it is delivered on time. The purpose of Intelligence is to serve to those responsible for making decisions so they can do it in an informed way. There is no use of it if it is not delivered before the decision has to be made.
All this means that when we talk about intelligence, we are not only referring to the product itself, but also to all the processes that make the product possible, which we are going to cover in full further ahead.
Finally, we can classify intelligence according to the time dedicated to study a specific subject, distinguishing between long‑term and short‑term intelligence; or according to its form: strategic, tactic or operational intelligence. In this case, the intelligence delivered will vary depending on which recipients are going to receive it.
Strategic level
Strategic intelligence informs the top decision makers, what is usually call the C‑Suite: CEO, CFO, COO, CIO, CSO, CISO and any other chief executive to which the information could be relevant. The intelligence delivered at this level must help them understand the threat they are up against. The decision makers should get a proper sense of what are the threat capabilities and motivations (disruption, theft of proprietary information, financial gain…) and of what are the probabilities of being a target as well as the possible consequences of it.
Operational level
Operational intelligence is destined to those making the day to day decisions, those in charge of defining priorities and allocating resources. To complete these tasks more efficiently, the intelligence team should provide them with information regarding which groups may target the organization and which are the ones that have been most recently active.
The deliverable might include CVEs and information regarding tactic and techniques of the possible threat. For example, this could be use to asses the urgency to patch certain systems or to add new security layers that will difficult the access to them among other things.
Tactical level
Tactical intelligence should be delivered to those in need of instantaneous information. The recipients should have a complete understanding of what adversary behaviors should they be paying attention to in order to identify the threats that could target the organization.
In this case, the deliverable may include IP addresses, domains and URLs, hashes, registry keys, email artifacts, etc. For example, these could be used to provide context to an alert and evaluate if it is worth involving the Incident Response (IR) team.
So far we have defined the concept of intelligence, cyber threat intelligence and the intelligence level, but what is that we understand by threat in the cyber realm?
We define as threat any circumstance or event that has the potential to exploit vulnerabilities and negatively impact operations, assets (including information and information systems), individuals, and other organizations or societies of an entity.
The main areas of interest of cyber threat Intelligence are cybercrime, hacktivism and cyber espionage. All of which can be roughly defined as organized groups that use technology to infiltrate in public and private organizations and governments to steal proprietary information or cause damage to its assets. Although, this doesn’t mean that other types of threats, like criminals or insiders, are out of the scope of interest.
Sometimes the terms threat actor and Advanced Persistent Threat (APT) are used as interchangeable, but the truth is that although we can say that every APT is a threat actor, not every threat actor is advanced or persistent. What distinguish an APT is a high level of OPSEC1 (operational security), combined with a low detection rate and a high level of success. Keep in mind that this might not apply perfectly to all the APT groups. For example, there are some groups that feed from the propaganda from the attack, so they put a lower effort on being identified.
To generate valuable intelligence is important to work with clear and defined concepts to structure the data and generate information. It is not mandatory to choose an existing terminology, but the MITRE Corporation has developed the Structured Threat Information Expression (STIX) (https://oasis-open.github.io/cti-documentation/) in order to facilitate the standardization and sharing of threat intelligence.
So, if we follow the STIX Definition (https://stixproject.github.io/data-model/), threat actors are “actual individuals, groups, or organizations believed to be operating with malicious intent.” Any threat actor could be defined by:
- Its type (https://stixproject.github.io/data-model/1.1/stixVocabs/ThreatActorTypeVocab-1.0/)
- Its motivations (https://stixproject.github.io/data-model/1.1/stixVocabs/MotivationVocab-1.1/)
- Its sophistication level (https://stixproject.github.io/data-model/1.1/stixVocabs/ThreatActorSophisticationVocab-1.0/)
- It intended effect (https://stixproject.github.io/data-model/1.1/stixVocabs/IntendedEffectVocab-1.0/)
- The campaigns it was involved in
- Its TTPs(Tactics, Techniques and Procedures: https://stixproject.github.io/data-model/1.2/ttp/TTPType/).
In summary, cyber threat intelligence is a tool that should be used to gain better insight into the threat actors’ interests and capabilities. It should be used to inform all the teams involve in securing and directing the organization.
To generate good intelligence it is necessary to define the right set of requirements, for which it’s crucial to understand the needs of the organization. Once this first step has been accomplished, we can better prioritize the threats the team should be focusing on and start monitoring those threat actors that might have the organization among its desired targets. Avoiding the collection of unnecessary data will help to better allocate time and resources, as well as to set the primary focus on the threats that are more imminent to the organization.
As Katie Nickels stated in her talk “The Cycle of Cyber Threat Intelligence“ (2019, https://www.youtube.com/watch?v=J7e74QLVxCk), the Cyber Threat Intelligence team is going to be influenced by where it gets set in, so to have it at a central position in the structure of the organization will help the team to actually support different functions. This is visualised below:
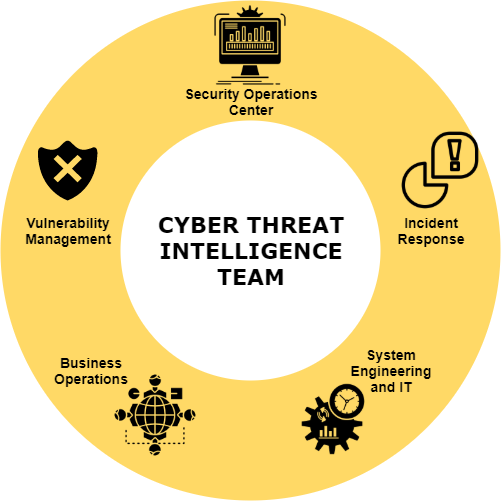
[…]





































































