Processing and Exploitation
After collection, the data must be processed and exploited to be converted into intelligence. The IOCs must be provided with context and its relevance and reliability must be assessed.
A way to approach to it is to break data into buckets and take advantage of available frameworks to look for patterns.
We are going to quickly review three of the most use intelligence frameworks: The Cyber Kill Chain, the Diamond Model and the ATT&CK Framework. The latter will have a full chapter dedicated to it later on.
The Cyber Kill Chain®
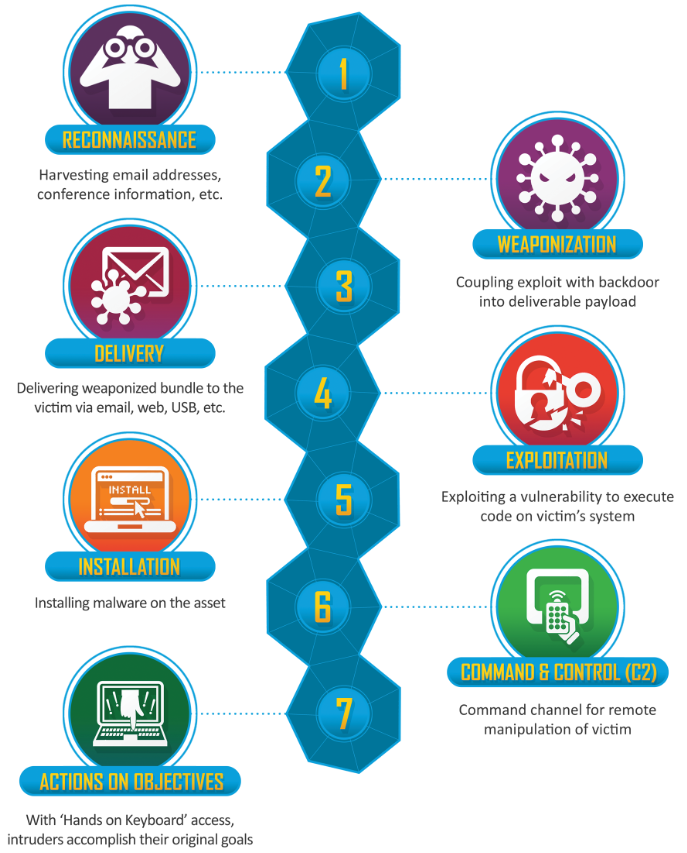
Developed by Lockheed Martin, the Cyber Kill Chain® is a means to identify the steps the threat actor should follow in order to achieve their objective.
It differentiates seven different steps:
- Reconaissance: process of getting to know the victim using noninvasive techniques.
- Weaponization: generating the exploit that is going to be delivered.
- Delivery: delivering the weaponized artifact.
- Exploitation: achieving code execution on the victim´s system through the exploitation of a vulnerability.
- Installation: installing the final malware piece.
- Command and Control (C2): establishing a channel to communicate with the malware on the victim´s system.
- Actions on objectives: with full access and communication, the attacker achieves his goal.This model has been criticized for not being good enough to describe the way some modern attacks work, but at the same time has been praise for delimiting the points in which an attack can be stopped.
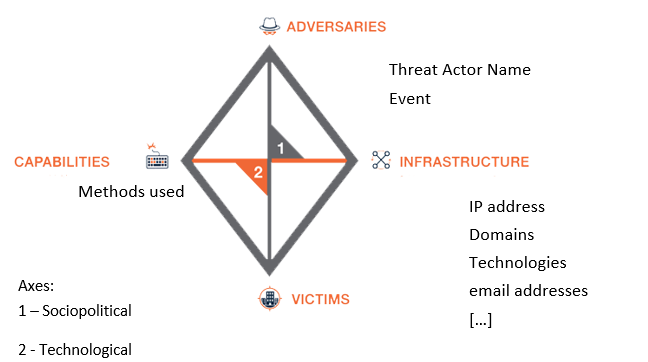
The Diamond Model
The Diamond Model provides a simple way to track breach intrusions, since it helps to establish the atomic elements involved in them. It is composed of four main features: adversary, infrastructure, capability and victim. These are for features are connected by the sociopolitical and the technical axes.
We will now have a look at the MITRE ATT&CK Framework.
MITRE ATT&CK Framework
The MITRE ATT&CK™ Framework is a descriptive model used to label and study the activities that a threat actor is capable of carrying out in order to get foothold and operate inside an enterprise environment, a cloud environment, smartphones or even inside industrial control systems.
The magic behind the ATT&CK™ framework is that it provides a common taxonomy for the cyber security community to describe the adversary behavior. It works as a common language that both offensive and defensive researchers can use to better understand each other and to better communicate with people not specialized in the field.
And on top of that you not only can use it as you see fit, but you can also build on top of it, creating your own set of tactics, techniques an procedures (TTPs).
There are 12 tactics used to encompass different set of techniques. Each tactic represents a tactical goal, i.e., the reason why the threat actor is showing a specific behavior. Each of these tactics is composed by a set of techniques and subtechniques that describes specific threat actor behaviors The procedure is the specific way in which a threat actor implements a specific technique or subtechnique. One procedure can expand into multiple techniques and subtechniques too.

We will now have a look at bias and analysis.





































































