Password profiling with CeWL
With every penetration test, reconnaissance must include a profiling phase in which we analyze the application, department or process names, and other words used by the target organization. This will help us to determine the combinations that are more likely to be used when the need to set a user name or password comes to the personnel.
In this recipe, we will use CeWL to retrieve a list of words used by an application and save it for when we try to brute-force the login page.
How to do it...
As the first step, we will look at CeWL's help to have a better idea of what it can do. In the terminal, type:
cewl --help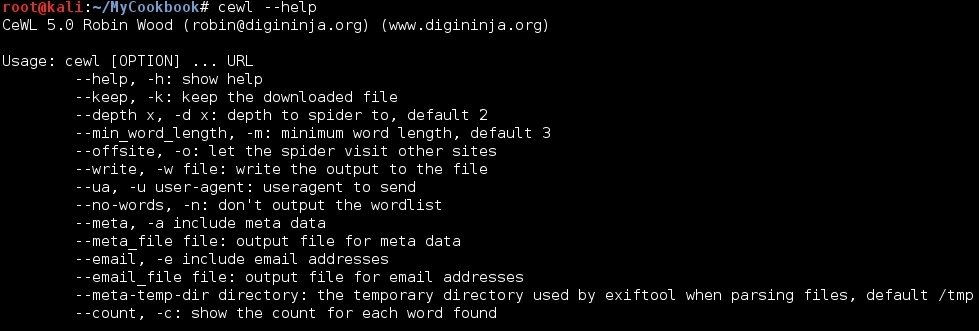
We will use CeWL to get the words on the WackoPicko application from vulnerable_vm. We want words with a minimum length of five characters; show the word count, and save the results to
cewl_WackoPicko.txt:cewl -w cewl_WackoPicko.txt -c -m 5 http://192.168.56.102/WackoPicko/Now, we open the file that CeWL just created and see a list of "word count" pairs...
























































