Managing Vulnerabilities
As I mentioned earlier, you must know your environment better than an attacker and use that attacker's mind‐set in key controls to develop your security program. Now that you have all the open‐source tools to troubleshoot your network and you know what assets you have to protect, you have to be able to assess those assets for vulnerabilities. It is a cyclic endeavor, as shown in Figure 4.1.
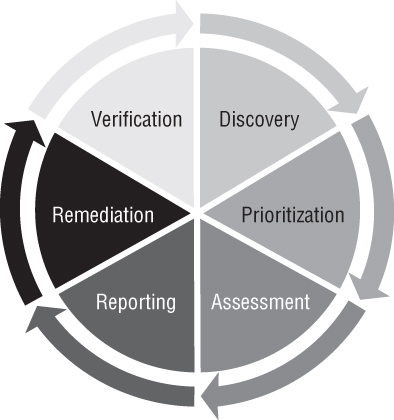
Figure 4.1: The vulnerability management lifecycle
In the discovery phase, you have to figure out what is on your network communicating to other devices. You cannot protect what you don't know you have. Once you're able to map out the assets, hosts, nodes, and intermediary devices on your network, then you're able to move to the next step.
Not all devices are created equal. A domain is a group of computers and other devices on a network that are accessed and administered with a common set of rules. A Windows domain controller (DC) is a...

























































