Exploiting routers
Previously, we saw how to exploit routing protocols. Now it is time to learn how to exploit modern routers.
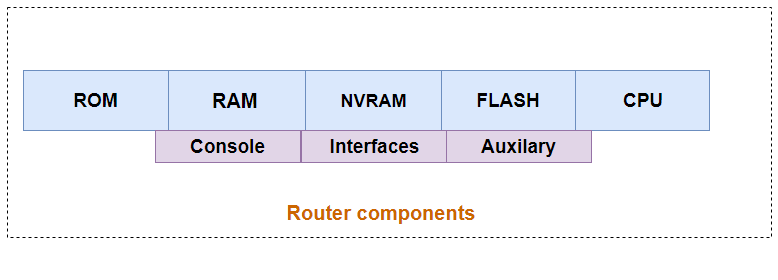
Router components
Like every major networking device, a router is composed of many internal components:
- CPU: Executes system operations
- RAM: Used to store instructions
- ROM: Contains boot instructions
- Flash: Contains the IOS
- NVRAM: Contains the startup configuration file:
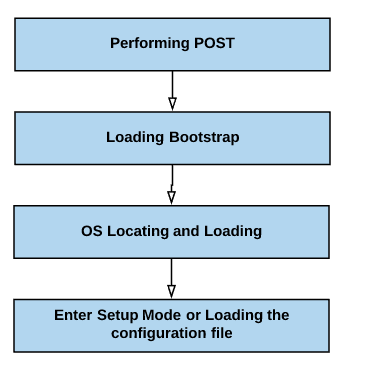
Router bootup process
To boot up, every major router goes through multiple steps:
- First, the router performs a POST.
- It loads the bootstrap.
- It locates and loads the operating system.
- You can choose between entering setup mode or loading the configuration file:
Router attacks
You learned about routing protocol threats, and now we will discuss attacks against routers; even the hardware faces many challenging threats:
- DDoS attack
- Man-in-the-middle attack
- Router firmware attacks
The router exploitation framework
The Routersploit framework is an open source tool to exploit router-embedded systems. You can clone it from...





































































