Using LUKS disk encryption
In enterprises, small business, and government offices, the users may have to secure their systems in order to protect their private data, which includes customers details, important files, contact details, and so on. To help with this, Linux provides a good number of cryptographic techniques that can be used to protect data on physical devices such as hard disk or removable media. One such cryptographic technique is using Linux Unified Key Setup (LUKS)-on-disk-format. This technique allows the encryption of Linux partitions.
This is what LUKS does:
- The entire block device can be encrypted using LUKS; it's well suited for protecting the data on removable storage media or the laptop disk drives
- LUKS uses the existing device mapper kernel subsystem
- It also provides passphrase strengthening, which helps protect against dictionary attacks
Getting ready
For the following process to work, it is necessary that a separate partition is also created while installing Linux, which will be encrypted using LUKS.
Note
Configuring LUKS using the steps given will remove all data on the partition being encrypted. So, before starting the process of using LUKS, make sure you take a backup of the data to some external source.
How to do it...
To begin with manually encrypting directories, perform the following steps:
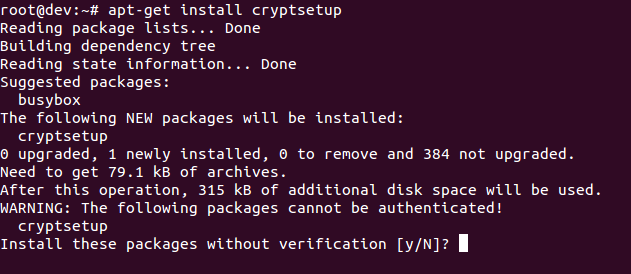
- Install
cryptsetupas shown here, which is a utility used for setting up encrypted filesystems:
apt-get install cryptsetupThe preceding command generates the following output:
- Encrypt your
/dev/sdb1partition, which is a removable device. To encrypt the partition, type the following command:
cryptsetup -y -v luksFormat /dev/sdb1The preceding command generates the following output:
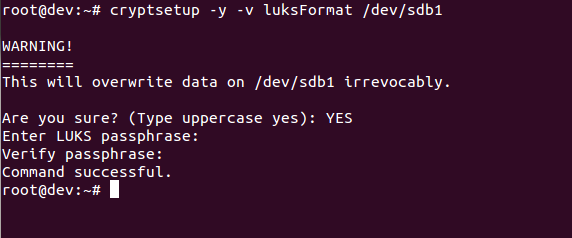
This command initializes the partition and also sets a passphrase. Make sure you note the passphrase for further use.
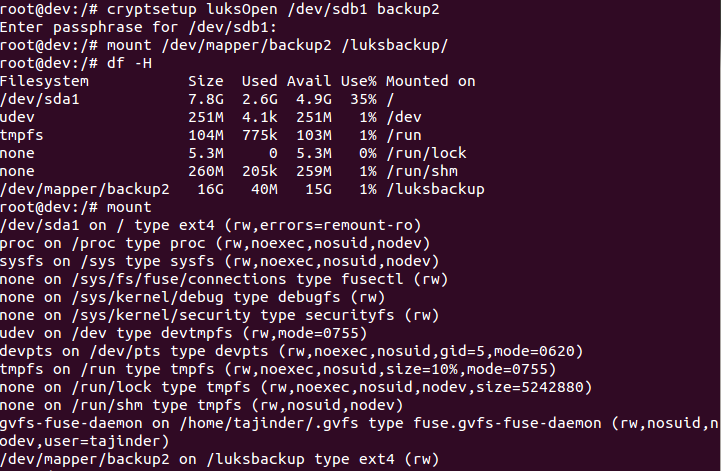
- Now open the newly created encrypted device by creating a mapping:
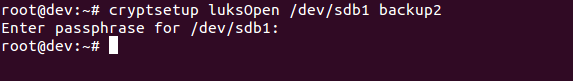
- Check to confirm that the device is present:
ls -l /dev/mapper/backup2The preceding command generates the following output:
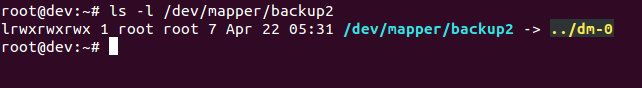
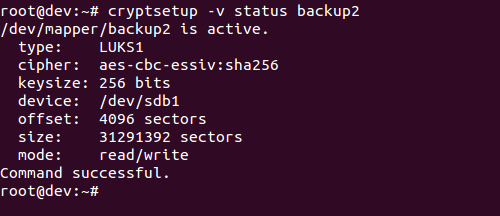
- Check the status of the mapping using the following command:
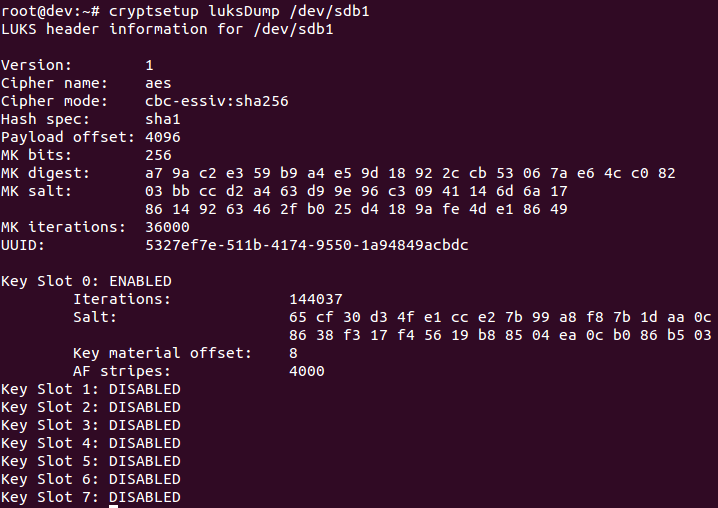
- Dump LUKS headers using the following command:
- Next, write zeros to
/dev/mapper/backup2encrypted device: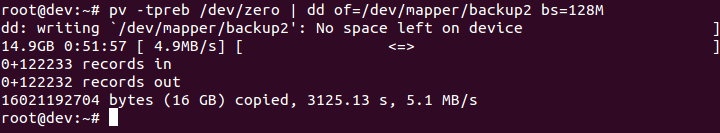
As the dd command may take hours to complete, we use the pv command to monitor the progress.
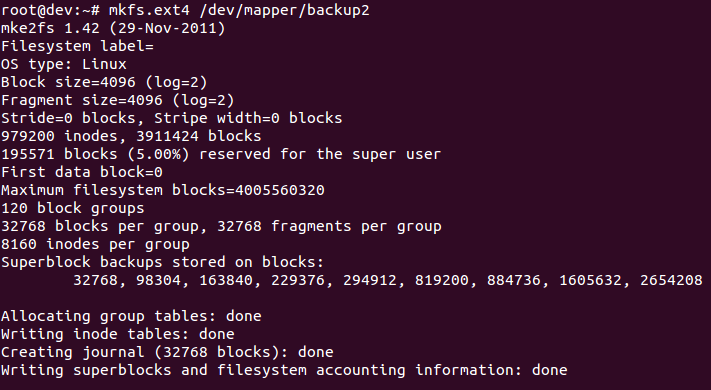
- Now create a filesystem:
mkfs.ext4 /dev/mapper/backup2The preceding command generates the following output:
- Then mount the new filesystem and confirm the filesystem is visible:
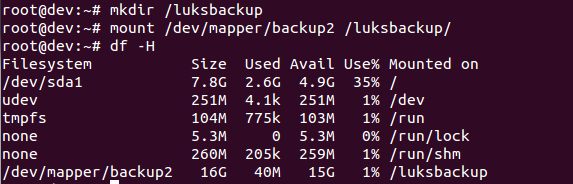
Congratulations! You have successfully created an encrypted partition. Now, you can keep all your data safe, even when the computer is off.
There's more...
Perform the following commands to unmount and secure the data on the partition:
umount /backup2 cryptsetup luksClose backup
To remount the encrypted partition, perform the following steps:
cryptsetup luksOpen /dev/xvdc backup2 mount /dev/mapper/backup2 /backup2 df -H mount