Applying RBAC policies to projects
Before an RBAC policy can be created, you need to have a network or QoS policy that you wish to share among a subset of projects. In the following sections, we will create projects, roles, users, and networks, and I will demonstrate how an access control policy limits the visibility and use of shared resources between the projects versus the default behavior of the shared attribute.
Creating projects and users
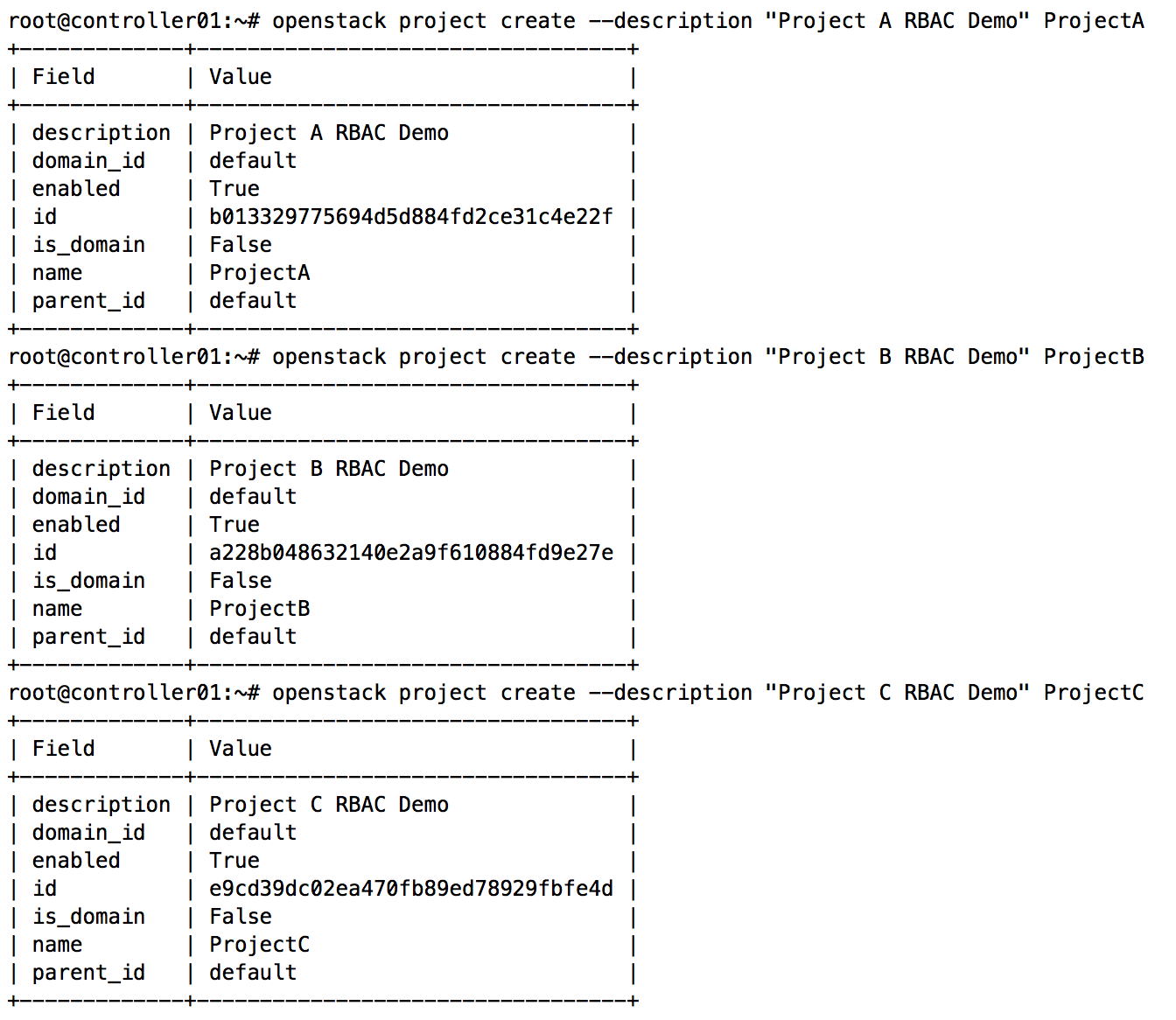
Using the openstack client, let's create three projects named ProjectA, ProjectB, and ProjectC, as shown here:
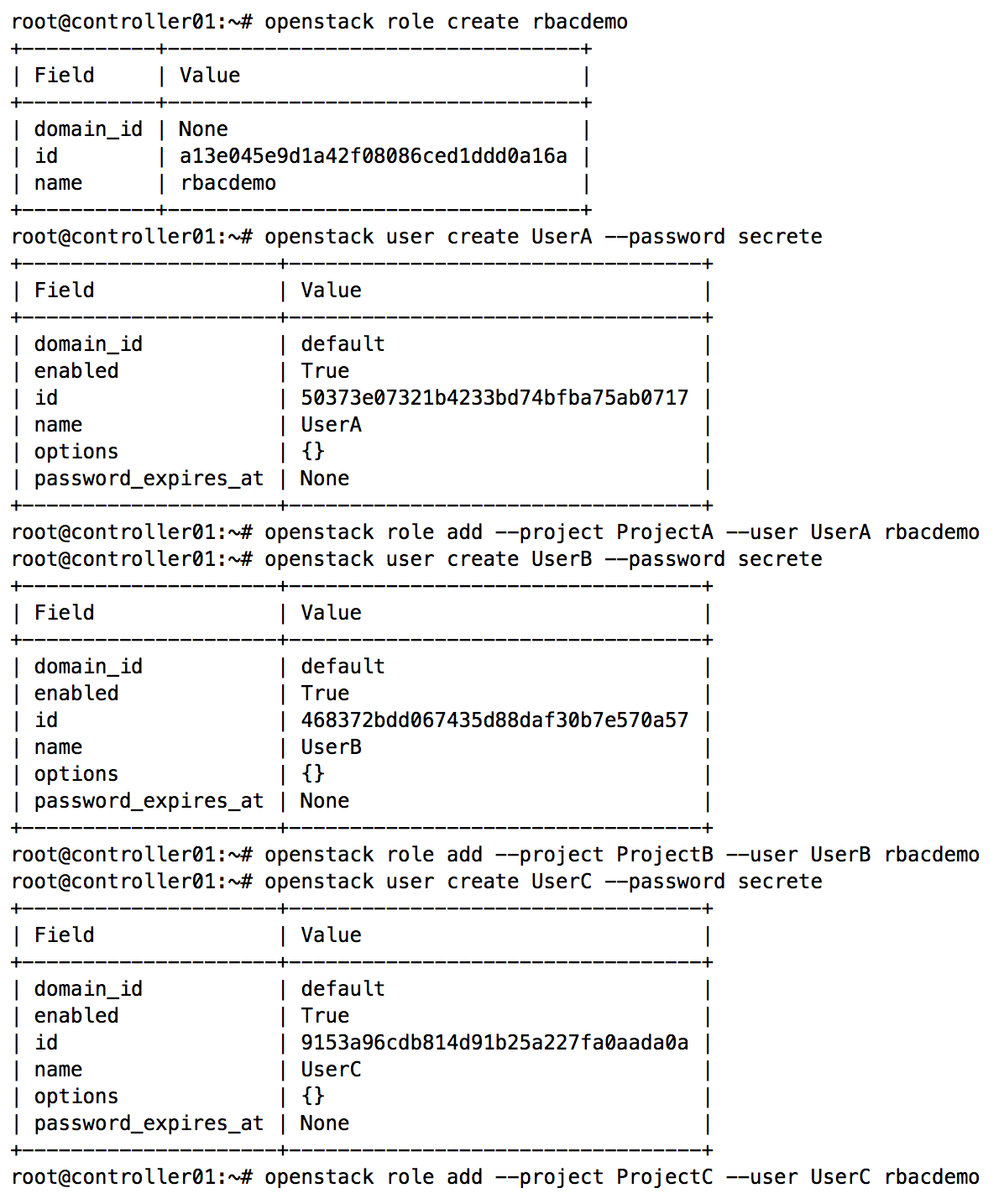
Using the openstack client, create a role named rbacdemo. Then, create a user in each project and apply the rbacdemo role to each user:
Creating a network to share
Using the openstack client, create a network named MySemiSharedNetwork and a subnet named MySemiSharedSubnet as the admin user. This network will be shared among some of the newly created projects:

In the network details, observe that the shared attribute of the network is set to False...




































































