Threat modeling IoT device hardware
It is time to analyze hardware threats for our target DVR. Most consumer DVRs are easy to open up and disassemble to examine their various inputs as well as their peripherals. This is due to the need to expand storage space or simply because they are not designed to be heavy duty like production hardware security modules (HSMs) which have tamper protections in place.
How to do it...
In this exercise, we use https://draw.io diagrams to help us with demonstrating hardware inputs.
Step 1: Creating an architecture overview and decomposition
The following is a diagram of the DVR's hardware:
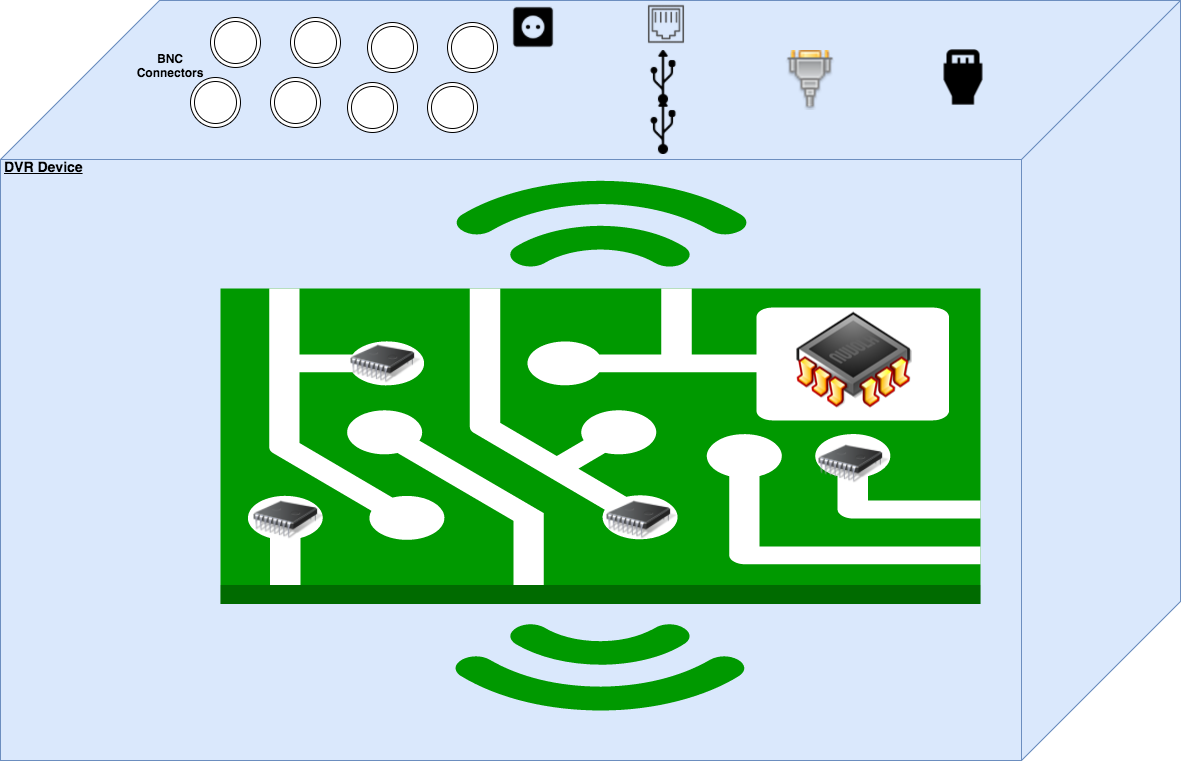
Depicting the image, there are eight BNC connectors for cameras, two USB ports, one Ethernet port, one power port, a VGA, and an HDMI port facing the outside of the DVR. Inside the DVR are various chips, with one being an EEPROM and possible inputs for UART on the PCB board itself.
Step 2: Identifying threats
An attacker could exploit the DVR hardware inputs to do the following...





































































